National Security Agency: Difference between revisions
imported>Howard C. Berkowitz (flow edit) |
mNo edit summary |
||
| (93 intermediate revisions by 6 users not shown) | |||
| Line 1: | Line 1: | ||
{{subpages}} | {{subpages}} | ||
The '''National Security Agency (NSA)''', formally the | {{TOC|right}} | ||
The '''National Security Agency (NSA)''', formally the ''National Security Agency/Central Security Service'', is part of the [[United States Department of Defense|U.S. Department of Defense]] and also the U.S. intelligence community . Its headquarters are at [[Fort Meade]], [[Maryland (U.S. state)|Maryland]], although it has worldwide installations.[[Image:NSA main HQ.jpg|thumb|View of part of headquarters complex]] The headquarters, which consists of several large buildings, an impressive fence, and acres of parking lots, is reputed to have the most computers of any place on earth. | |||
In its name, national security was selected as deliberately vague and euphemistic; the very existence of the organization was originally [[classified information|classified]]. It has dual responsibilities: | |||
:#As a member of the | :#As a member of the United States intelligence community , it has the principal responsibility for collecting and processing signals intelligence. | ||
:#As the agency responsible for the "Information Assurance mission [to provide] the solutions, products, and services, and [conduct] defensive | :#As the agency responsible for the "Information Assurance mission [to provide] the solutions, products, and services, and [conduct] defensive information operations, to achieve information assurance for information infrastructures critical to U.S. national security interests"<ref name=NSAMission>{{citation | ||
| author = National Security Agency | | author = National Security Agency | ||
| title = Mission Statement | | title = Mission Statement | ||
| url = }}</ref> | | url = http://www.nsa.gov/about/index.shtml}}</ref> The abbreviation "NSA" is not infrequently and facetiously explained as "no such agency" or "never say anything". In fact, there have even been more secret intelligence organizations; the "fact of" the existence of the [[National Reconnaissance Office]] (NRO) remained classified for many more years. Smaller organizations, such as the U.S. Special Operations Command organization originally called the [[Intelligence Support Agency]], is reported to change its classified English-language name every two years, and the code word for it every six months — or immediately if the code becomes public. | ||
Immediately outside one of the security gates is the National Cryptologic Museum and the National Vigilance Park, the latter holding three aircraft, one from each service, and of a type that was lost during SIGINT operations. | Immediately outside one of the security gates is the National Cryptologic Museum and the National Vigilance Park, the latter holding three aircraft, one from each service, and of a type that was lost during SIGINT operations. | ||
| Line 13: | Line 14: | ||
SIGINT personnel not only died on duty in aircraft. The first U.S. soldier killed in Vietnam belonged to an Army SIGINT unit. A large number of personnel were killed in the Israeli attack on the SIGINT ship, ''USS Liberty''. | SIGINT personnel not only died on duty in aircraft. The first U.S. soldier killed in Vietnam belonged to an Army SIGINT unit. A large number of personnel were killed in the Israeli attack on the SIGINT ship, ''USS Liberty''. | ||
==Executive | ==Organization== | ||
The '''[[Director, National Security Agency]](DIRNSA)/Chief, Central Security Service''' is an active-duty, three-star officer from one of the military services. The [[Deputy Director, National Security Agency]] is a career civilian. Two senior officials are | NSA has several kinds of organizational relationships. It has its own leadership, its specific relation to military organizations through its Central Security Service authority, to the United States intelligence community (IC), certain foreign countries, and participation and education in technologies relevant to its work. | ||
===Executive structure=== | |||
The '''[[Director, National Security Agency]](DIRNSA)/Chief, Central Security Service''' is an active-duty, three- or four-star officer from one of the military services. The [[Deputy Director, National Security Agency]] is a career civilian. Two senior officials are the Signals Intelligence Director (SID) and the Information Assurance Director (IAD). There are usually some very senior staff specialists bearing titles such as Chief Cryptologist. | |||
[[Keith Alexander|Keith B. Alexander]], serving as DIRNSA as a [[lieutenant general]], [[U.S. Army]], was nominated for promotion to full general in October 2009. | |||
NSA and | ===NSA and the U.S. intelligence community=== | ||
As mentioned, NSA is part of the United States intelligence community . | |||
While the exact | NSA also is the lead agency for [[counterintelligence#operations security|Operations Security]] (OPSEC), a counterintelligence function within government that goes beyond communications security. | ||
===International=== | |||
NSA and its predecessors have had a very close relationship with its British Counterpart, the Government Communications Headquarters (GCHQ). The resident U.S. representative there, the Senior U.S. Liaison Officer (SUSLO) holds what is considered a key position. There are also significant liaison relationships with Australia, Canada, and New Zealand, as well as with alliances such as [[NATO]]. With increasingly diverse membership in organizations such as NATO, there are increasing problems as to the extent of classified information, especially in a compartmented control system, as used for intelligence and communications security information. | |||
===Internal organization=== | |||
While the exact organization is classified, and has varied over time, it will generally contain functions including: | |||
:*National level SIGINT-collection management and operations | :*National level SIGINT-collection management and operations | ||
:*Coordination of tactical SIGINT | :*Coordination of tactical SIGINT | ||
:*Advanced research and development. NSA is reputed to be the world's largest employer of mathematicians. | :*Advanced research and development. NSA is reputed to be the world's largest employer of mathematicians. | ||
:*Computing and telecommunications services, usually including research | |||
:*Computing and communications security doctrine and education available to non-military, non-intelligence agencies of government, and frequently to the public. Unclassified security work in this area is often joint with the [[National Institutes for Standards and Technology]] | |||
:*SIGINT processing organizations, generally organized on a regional basis depending on national priorities. NSA is not considered to be an analytic agency that produces "finished intelligence", although, by all indications, it will report on the patterns of COMINT and ELINT information, rather than the content, for example, of messages read through COMINT. | :*SIGINT processing organizations, generally organized on a regional basis depending on national priorities. NSA is not considered to be an analytic agency that produces "finished intelligence", although, by all indications, it will report on the patterns of COMINT and ELINT information, rather than the content, for example, of messages read through COMINT. | ||
:*Defensive information operations, including creating, either in-house or on contract, U.S. COMSEC equipment for classified communications, and [[cryptographic keying material]] for classified and certain other types of sensitive but unclassified government communications. | :*Defensive information operations, including creating, either in-house or on contract, U.S. COMSEC equipment for classified communications, and [[cryptographic keying material]] for classified and certain other types of sensitive but unclassified government communications. | ||
== | ==Legal authority== | ||
Originally created by Executive Order as a result of a National Security Council directive, NSA is routinely funded in the classified IC budget appropriated by the Congress and signed by the President. | |||
===Authority with respect to U.S. citizens=== | |||
In general, NSA is not intended to participate in domestic law enforcement, or in domestic investigation except for its own personnel security clearances and similar purposes. It has tended to operate more under IC and U.S. Communications Security Board regulations than under explicit legislation. | |||
====1950s programs==== | |||
During this period, several programs, potentially in violation of its foreign intelligence charter, the NSA (and its AFSA predecessor) monitored international telegram and selected voice communications of American citizens<ref name=SenateNSA75>{{citation | |||
| last =Senate Select Committee to Study Government Operations with Respect to Intelligence Activities | |||
| title = The National Security Agency and Fourth Amendment Rights | |||
| date = OCTOBER 29 AND NOVEMBER 6, 1975 | |||
| url = http://cryptome.org/nsa-4th.htm#Exhibit%203 | |||
| accessdate = 2007-12-07}}</ref>.[[Project SHAMROCK]], started during the fifties under AFSA, the predecessor of NSA, and terminated in 1975, was a program in which [[NSA]] obtained copies, without a warrant, of telegrams sent by international record carriers. The related [[Project MINARET]] intercepted voice communications of persons of interest to US security organizations of the time, including Malcolm X, Jane Fonda, Joan Baez, and Martin Luther King. | |||
====Programs terminated in the 1970s==== | |||
=== US domestic surveillance by NSA === | |||
A Senate Select Committee, generally called the Church Committee, began some of the first public hearings on US intelligence. These hearings revealed information that was questionably legal, and led to the termination of some programs, such as [[Project SHAMROCK]] and [[Project MINARET]], as well as enacting, in 1978, the [[Foreign Intelligence Surveillance Act]] (FISA). FISA established guidelines for COMINT involving US citizens, and established a special FISA Court to approve warrants. The FISA judges were cleared for all intelligence information relevant to warrant requests. | |||
During these hearings, the Director of NSA, LTG [[Lew Allen]], discussed targeting of information, including the names of American citizens, in '''watch lists''': "The use of lists of words, including individual names, subjects, locations, et cetera, has long been one of the methods used to sort out information of foreign intelligence value from that which is not of interest. In the past such lists have been referred to occasionally as watch lists, because the lists were used as an aid to watch for foreign activity of reportable intelligence interest. However, these lists generally did not contain names of U.S. citizens or organizations. The activity in question is one in which U.S. names were used systematically as a basis for selecting messages, including some between U.S. citizens, when one of the communicants was at a foreign location." | |||
[[Richard M. Nixon]] ordered the CIA to gather information on foreign sources of controlled substances and how they entered the US. As part of this initiative, the [[Drug Enforcement Administration#Predecessors|Bureau of Narcotics and Dangerous Drugs]] (BNDD) requested NSA COMINT related to foreign drug traffic, including watch lists with some U.S. names. International drug trafficking became a formal US Intelligence Board (USIB) requirement in 1971. Other target names for watch lists, concerned with [[North Vietnam]], came from the [[Defense Intelligence Agency]]. | |||
During the hearings, LTG Allen said he had received a letter, on [[October 1]], 1973, from [[Attorney General]] [[Elliot Richardson]] "indicating that he was concerned with respect to the propriety of requests for information concerning U.S. citizens which NSA had received from the FBI and Secret Service. He wrote the following: | |||
"Until I am able more carefully to assess the effect of Keith and other Supreme Court decisions concerning electronic surveillance upon your current practice of disseminating to the FBI and Secret Service information acquired by you through electronic devices pursuant to requests from the FBI and Secret Service, it is requested that you immediately curtail the further dissemination of such information to these agencies." <ref name=SenateNSA75 /> | |||
====1990s policy==== | |||
For a number of years, United States Signals Intelligence Directive (USSID) 18<ref name=USSID18>{{citation | |||
| title = United States Signals Intelligence Directive (USSID) 18 | |||
| author = National Security Agency/Central Security Service | |||
| date = 27 July 1993 | |||
| url =http://www.gwu.edu/~nsarchiv/NSAEBB/NSAEBB23/07-01.htm}}</ref> was the policy document governing its interception of the communications of U.S. citizens. This document, which has largely been declassified, may no longer be the primary guidance, as there are controversial claims, by the [[George W. Bush]] Administration, of an inherent Presidential authority for [[warrantless surveillance]] as part of the national security. | |||
Other relevant regulations come from the Department of Defense <ref name=DOD4240.1-R>{{citation | |||
| title = Department of Defense Regulation 4240.1-R: Procedures governing the activities of DOD intelligence components that affect United States persons | |||
| date = December 1982 | |||
| author = Under Secretary of Defense for Policy | |||
|url = http://cryptome.org/dod5240-1-r.htm}}</ref> and the Department of Justice <ref name=DOJ>{{citation | |||
| title = Attorney General Guidelines for FBI Foreign Intelligence Collection and Foreign Counterintelligence Investigations | |||
| author = [[United States Attorney General]] | |||
| url =http://cryptome.org/fbi-guide.htm | |||
| date = 18 April 1983 | |||
}}</ref> | |||
It is possible to obtain warrants for interception of communications, by divulging all probable cause to a judge of the [[Foreign Intelligence Surveillance Court]] (FISC), who is cleared for all classified information. The FISC is authorized by the [[Foreign Intelligence Surveillance Act]] of 1978. | |||
====Recent US domestic surveillance issues==== | |||
Under the [[George W. Bush]] administration, there has been a large-scale and controversial capture and analysis of domestic and international telephone calls, claimed to be targeted against terrorism. It is generally accepted that warrants have not been obtained for this activity, sometimes called [[Room 641A]] after a location, in San Francisco, where AT&T provides NSA access. While very little is known about this system, it may be focused more on the signaling channel and [[Call detail record]]s than the actual content of conversations. | |||
Another possibility is the use of software tools that do high-performance deep packet inspection. According to the marketing VP of Narus, "Narus has little control over how its products are used after they're sold. For example, although its lawful-intercept application has a sophisticated system for making sure the surveillance complies with the terms of a warrant, it's up to the operator whether to type those terms into the system... | |||
"That legal eavesdropping application was launched in February 2005, well after whistle-blower Klein allegedly learned that AT&T was installing Narus boxes in secure, NSA-controlled rooms in switching centers around the country. But that doesn't mean the government couldn't write its own code to do the dirty work. Narus even offers software-development kits to customers ".<ref name=NarusWired>{{Citation | |||
| last = Singel | |||
| first = Ryan | |||
| title = Whistle-Blower Outs NSA Spy Room | |||
| journal = Wired | |||
| date = 04.07.06 | |||
| year = 2006 | |||
| url = http://www.wired.com/science/discoveries/news/2006/04/70619 | |||
| id = ATTWired | |||
}}</ref> The same type of tools with legitimate ISP security applications also have COMINT interception and analysis capability. | |||
Former AT&T technician [[Mark Klein]], who revealed AT&T was giving NSA access, | |||
said in a statement, said a Narus STA 6400 was in the NSA room to which AT&T allegedly copied traffic. The Narus device was "known to be used particularly by government intelligence agencies because of its ability to sift through large amounts of data looking for preprogrammed targets."<ref name=NarusWired /> | |||
In 2006 the [[Electronic Frontier Foundation]] (EFF) brought a class action suit, ''Hepting v. AT&T'', against AT&T for allegedly illegally assisting the NSA in a massive program of warrantless wiretaps. Much of their evidence came from Klein. An EFF [http://www.eff.org/nsa/hepting web page] has extensive information, including court documents. Quoting that page: "By providing the NSA with unfettered access to their telecommunications infrastructure — all without warrants or legal order -- AT&T is guilty of violating the Foreign Intelligence Surveillance Act (FISA) as well as the Fourth Amendment". | |||
In June 2008, Congress passed the [[FISA Amendments Act]] (FAA), retroactively granting AT&T and other telecommunications companies immunity from prosecution in such cases. As of late 2008, the EFF is both lobbying Congress to rescind that act and challenging it in court as unconstitutional. They have also filed another suit, ''Jewel vs NSA'', this time directly against NSA with [[George Bush]], [[Dick Cheney]] and others as co-defendants. Again, they have a [http://www.eff.org/cases/jewel web page] with information including court documents. | |||
==Creation of NSA== | |||
{{seealso|SIGINT in the Second World War}} | {{seealso|SIGINT in the Second World War}} | ||
During the Second World War, the Army and Navy had separate | During the Second World War, the Army and Navy had separate signals intelligence and [[communications security]] organization, which coordinated only informally. Depending on the service, tactical SIGINT, cryptologic development, strategic SIGINT, and cryptologic operations might be performed by autonomous organizations within a service department. | ||
After the end of World War II, all the Western allies began a rapid drawdown. At the end of WWII, the US still had a COMINT organization split between the Army and Navy. | After the end of World War II, all the Western allies began a rapid drawdown. At the end of WWII, the US still had a COMINT organization split between the Army and Navy. See SIGINT from 1945 to 1989 | ||
<ref name=NSAVN-1>{{citation | <ref name=NSAVN-1>{{citation | ||
| chapter = Chapter 1 - Le Grand Nombre Des Rues Sans Joie: [Deleted] and the Franco-Vietnamese War, 1950-1954 | | chapter = Chapter 1 - Le Grand Nombre Des Rues Sans Joie: [Deleted] and the Franco-Vietnamese War, 1950-1954 | ||
| Line 47: | Line 124: | ||
}}</ref> The Army Security Agency (ASA) had shared the national COMINT mission with the Navy's Communications Supplementary Activity (COMMSUPACT) - which became the Naval Security Group in June 1950. During and after World War II, a portion of Army COMINT assets was dedicated to support of the U.S. Army Air Corps, and, when the independent Air Force was created in 1947, these cryptologic assets were resubordinated to the new organization as the Air Force Security Service (AFSS). | }}</ref> The Army Security Agency (ASA) had shared the national COMINT mission with the Navy's Communications Supplementary Activity (COMMSUPACT) - which became the Naval Security Group in June 1950. During and after World War II, a portion of Army COMINT assets was dedicated to support of the U.S. Army Air Corps, and, when the independent Air Force was created in 1947, these cryptologic assets were resubordinated to the new organization as the Air Force Security Service (AFSS). | ||
[[U.S. Secretary of Defense]] [[James Forrestal]] rejected the early service COMINT unification plans. The Department of State objected to the next draft, which put the Central Intelligence Group/Central Intelligence Agency in charge of national COMINT. | [[U.S. Secretary of Defense]] [[James Forrestal]] rejected the early service COMINT unification plans. The Department of State objected to the next draft, which put the Central Intelligence Group/Central Intelligence Agency in charge of national COMINT. As a compromise and to centralize common services, the '''Armed Forces Security Agency (AFSA)''', was formed by secret executive order in 1948. As opposed to NSA, AFSA did not have the authority for central control of individual service COMINT and COMSEC. Policy direction of COMINT came from the U.S. Communications Intelligence Board (USCIB) which, in April 1949, requested $22 million in funds, including 1,410 additional civilian employees, to expand the COMINT effort. | ||
===UKUSA Agreement=== | |||
While the details remain classified, there is a very high amount of signals intelligence cooperation among the five nations under a 1948 agreement, generally called the UKUSA Agreement | |||
{| class="wikitable" | |||
|- | |||
! Country | |||
! Agency | |||
|- | |||
| Australia | |||
| [[Defence Signals Directorate]] | |||
|- | |||
| Canada | |||
| [[Defence Canada#Communications Security Establishment|Communications Security Establishment]] | |||
|- | |||
| New Zealand | |||
| [[Government Communications Security Bureau]] (GCSB) | |||
|- | |||
| United Kingdom | |||
| Government Communications Headquarters (GCHQ) | |||
|- | |||
| United States | |||
| '''National Security Agency''' | |||
|} | |||
Since the geographic location of individual nations make them the optimal place to intercept signals from various worldwide targets, there is a considerable effort to distribute the interception workload and avoid duplication. The five countries appear to have near-total access to the others' raw intercepts and processed SIGINT, but not as much sharing of all-source finished intelligence. Even for finished intelligence, however, there is much exchange. | |||
For the Pacific, the USCIB targeted China, and Russia in both the European and Pacific theaters, but Korea was a low-priority target. <ref name=NSA-Korea>{{cite web | |||
| last =Hatch | |||
| first = David A. | |||
| coauthors = Robert Louis Benson | |||
| title = The Korean War: The SIGINT Background | |||
| publisher = National Security Agency | |||
| url = http://www.nsa.gov/publications/publi00022.cfm}}</ref> | |||
Korean coverage was incidental to Soviet and Chinese interests in the Korean Peninsula.<ref name=NSA-Korea /> Both the surprise attack, and the difficulty of rapidly enlarging the SIGINT organization, showed that the organization was imperfect. See [[Intelligence on the Korean War]] | |||
===NSA created=== | ===NSA created, but the services roll on=== | ||
President [[Harry Truman]], on 24 October 1952, issued a directive that set the stage for the National Security Agency, whose scope went beyond the pure military. NSA was created on 4 November 1952.<ref name=NSAorigin /> | President [[Harry Truman]], on 24 October 1952, issued a directive that set the stage for the National Security Agency, whose scope went beyond the pure military. NSA was created on 4 November 1952.<ref name=NSAorigin /> | ||
The Service Cryptologic Agencies still had their own identity, even after the formation of NSA. | The Service Cryptologic Agencies still had their own identity, even after the formation of NSA. They continued reorganizations independently of NSA; in 1955, ASA took over electronic intelligence (ELINT) and electronic warfare functions previously carried out by the Signal Corps. Since its mission was no longer exclusively identified with intelligence and security, ASA was withdrawn from G-2 control and resubordinated to the Army Chief of Staff as a field operating agency. | ||
Eventually, the individual service SIGINT organizations were to become Service Cryptologic Elements (SCE), with dual reporting to their local operational commands and to NSA/CSS -- and sometimes very little to the local command. The captain of the ''USS Pueblo'', a SIGINT ship, was discouraged from entering the SIGINT compartments of the ship. Pilots of SIGINT aircraft were told where to fly, but were not informed, in detail, what the technicians on board were doing -- unless the technicians issued an urgent warning of a hostile aircraft coming close. Several U.S. SIGINT aircraft were damaged or destroyed. | Eventually, the individual service SIGINT organizations were to become Service Cryptologic Elements (SCE), with dual reporting to their local operational commands and to NSA/CSS -- and sometimes very little to the local command. The captain of the ''USS Pueblo'', a SIGINT ship, was discouraged from entering the SIGINT compartments of the ship. Pilots of SIGINT aircraft were told where to fly, but were not informed, in detail, what the technicians on board were doing -- unless the technicians issued an urgent warning of a hostile aircraft coming close. Several U.S. SIGINT aircraft were damaged or destroyed. | ||
While the names were to continue to change, the main SCEs reorganized into units principally serving NSA's national-level goals, although there were also tactical SIGINT units within a dual chain of command. Since most NSA system was under | While the names were to continue to change, the main SCEs reorganized into units principally serving NSA's national-level goals, although there were also tactical SIGINT units within a dual chain of command. Since most NSA system was under compartmented control systems, local military commanders might not have the appropriate clearance. The phrase "behind the green door", from a song and a pornographic movie, became the euphemism for the [[Sensitive compartment information facility}sensitive compartment information facilities (SCIF), behind whose locked and guarded doors the actual SIGINT was done. | ||
{| class="wikitable" | {| class="wikitable" | ||
|- | |- | ||
| Line 81: | Line 180: | ||
| Air Force Security Service | | Air Force Security Service | ||
|} | |} | ||
=== | ===Coordinating the SCEs === | ||
A separate SIGINT and communications security organization, or Service Cryptologic Element (SCE), existed for the US Army, Navy, and Air Force. Some of the differences were quite appropriate to support of the military operations of the particular service; the Air Force would be interested ELINT about air defense radars that a bomber might take in attacking the Soviet Union over a polar route, while the Navy would be more interested in coastal air defense radars. The Army would want to be able to recognize hostile artillery fire control radars, and also how to do tactical direction finding, traffic analysis, and field-level [[cryptanalysis]] against opposing ground forces. | |||
All of these services also had capabilities to provide national-level intelligence more appropriate for NSA's mission than for support to military operation. The Army had both fixed and mobile intercept equipment appropriate for long-term listening to ground stations, while the Air Force and Navy could probe new foreign electronic systems as part of national-level intelligence goals. | |||
Even though NSA proper had been formed in 1952, the activities of the Service Cryptologic Agencies were not well coordinated. The Air Force and Navy, for example, might duplicate efforts in probing North Korean radars. Air Force RIVET JOINT RC-135 aircraft collected COMINT of interest to all the services. Navy P2 and P3 electronic capabilities also collected data of relevance to the military as a whole. | |||
Bamford described the first effort to organize the SCEs was to create a "fourth branch" of the military, which triggered intense bureaucratic resistance from the services. A compromise was reached by creating the [[Central Security Service]] (CSS). The Director of the NSA (DIRNSA) acquired a "second hat" as the commander of CSS. Just as the services rotated the DIRNSA assignment among their three-star (or three-star eligible) intelligence officers, the actual chief of CSS, reporting to DIRNSA, was a two-star post that also rotated among the services. <ref name=Bamford2001>{{cite book | |||
| title = Body of Secrets: Anatomy of the Ultra-Secret National Security Agency | |||
| first = James | last = Bamford | |||
| publisher = Doubleday | |||
| year = 2001 | |||
| ISBN-10 = 0385499078 | |||
}}</ref> Bamford describes CSS in different ways. At one point, he speaks of "a former senior NSA official who described it as 'a half-assed, last-minute job' designed to destroy the original fourth-service proposal." Later in the same book, however, draws attention, however, to the almost unparalleled power vested in the DIRNSA through NSCID No. 6, revised on 17 February 1972, "All instructions issued by the Director under the authority provided in this paragraph shall be mandatory, subject only to appeal to the Secretary of Defense." Thus, the DIRNSA is able to bypass "not only the Joint Chiefs, but even the secretaries of the branches" giving him his own SIGINT Army, Navy, Air Force, and Marines. | |||
The idea of a fourth service branch for SIGINT is not unheard of; "NSA’s Canadian cousin, the Communications Security Establishment (CSE) relies entirely upon the Canadian Forces Supplementary Radio System (CFSRS) for all raw SIGINT collection. CFSRS has been a part of the Canadian Forces Information Operations Group (CFIOG) since the latter was established 08 May 1998."<ref name=CSS-Clive>{{citation | |||
| title = NSA’s Central Security Service | |||
| first = Keith P. | last = Clive | |||
| url = http://www.fas.org/irp/eprint/css.htm | |||
| year = 2002 | |||
}}</ref> Clive uses the example of the Navy SCE, as of 2002, as showing the significance of organizations under CSS control: "the Naval Security Group (NSG) might be the best indicator of the significance of the military contribution to NSA’s SIGINT efforts. According to Steven Aftergood of the Federation of American Scientists (FAS), the NSG is responsible for "Signals Security matters and, for Data Link Vulnerability Assessment Methodology within the Navy Vulnerability Assessment Program." The Naval Security Group Command (NSGC) "coordinates with, tasks as appropriate, and appraises the efforts of commands and offices of the Department of the Navy and NSA/Central Security Service in the fulfillment of Navy logistics support requirements, as directed by the Secretary of Defense. It also participates in NSA studies as required." The cryptologic staff "work with some of the most sophisticated and complex systems the Navy has to offer in performance of their mission." NSGC’s Commander "reports to the Chief, Central Security Service (CSS) as the Navy Element Commander of the CSS and performs cryptologic functions at the National level as the Commander of the Navy's Service Cryptologic Element (SCE)." Considering just NSG’s structure, naval SIGINT, and by inference all military SIGINT, does not appear to be a mainly nominal entity. Certainly, with the information overload that the Internet has brought, even for NSA, they can use all the help they can get." | |||
==1950-1954: Strategic SIGINT == | |||
In the fifties, only aircraft platforms could obtain [[SIGINT from 1945 to 1989#Strategic SIGINT targeting of the USSR|SIGINT over the USSR]]. | |||
In [[SIGINT from 1945 to 1979#Indochina |Indochina ]], the French had a number of direction-finding stations, with about 40 technicians. They monitored Viet Minh, Nationalist and Communist Chinese, British, Dutch and Indonesian communications<ref name=NSAVN-1 /> In general, however, SIGINT in French Indochina was limited by the availability of linguists. <ref name=PikeFrenchSIGINT>{{citation | |||
| first = Pike | |||
| last = John | |||
| title = DGSE - General Directorate for External Security (Direction Generale de la Securite Exterieure) | |||
| url = http://www.globalsecurity.org/intell/world/france/dgse.htm | |||
}}</ref> | |||
US SIGINT | There are several ways to split US SIGINT regarding Southeast Asia into periods. In this article, the emphasis is on strategic systems; see SIGINT from 1945 to 1989 for both tactical details and more information on strategic operations. Gilbert's four periods are focused on the deployment of American units.<ref name=Gilbert>{{cite book | ||
| last = Gilbert | | last = Gilbert | ||
| first = James L. | | first = James L. | ||
| Line 157: | Line 219: | ||
| date = 2003 | | date = 2003 | ||
| location = Pittsburgh, PA | | location = Pittsburgh, PA | ||
| url = http://findarticles.com/p/articles/mi_qa3926/is_200401/ai_n9362058 }}</ref> | | url = http://findarticles.com/p/articles/mi_qa3926/is_200401/ai_n9362058 }}</ref> In contrast, Hanyok's periods <ref name=NSAVN-3>{{citation | ||
| chapter = Chapter 3 - "To Die in the South": SIGINT, the Ho Chi Minh Trail, and the Infiltration Problem, [Deleted] 1968 | | chapter = Chapter 3 - "To Die in the South": SIGINT, the Ho Chi Minh Trail, and the Infiltration Problem, [Deleted] 1968 | ||
| title = Spartans in Darkness: American SIGINT and the Indochina War, 1945-1975 | | title = Spartans in Darkness: American SIGINT and the Indochina War, 1945-1975 | ||
| Line 172: | Line 225: | ||
| publisher = Center for Cryptologic History, National Security Agency | | publisher = Center for Cryptologic History, National Security Agency | ||
| year = 2002 | | year = 2002 | ||
| url = http://www.fas.org/irp/nsa/spartans/chapter3.pdf }}</ref> | | url = http://www.fas.org/irp/nsa/spartans/chapter3.pdf }}</ref>, although the redactions make it difficult to see exactly why he created chapters as he did, but it would appear that he ties them more to VC/NVA activities, as well as RVN politics, than the US view. | ||
Although SIGINT personnel were present in 1960, Gilbert breaks the ASA involvement in Vietnam into four chronological phases, Although SIGINT personnel were present in 1960, Gilbert breaks the ASA involvement in Vietnam into four chronological phases,<ref name=Gilbert /> which do not match the more recent NSA history by Hanyok, which is less focused on events with the US military. <ref name=NSAVN-2>{{citation | |||
= | | chapter = Chapter 2 - The Struggle for Heaven's Mandate: SIGINT and the Internal Crisis in South Vietnam, [Deleted] 1962 | ||
| title = Spartans in Darkness: American SIGINT and the Indochina War, 1945-1975 | |||
| first1 = Robert J. | last1 =Hanyok | |||
| publisher = Center for Cryptologic History, National Security Agency | |||
| year = 2002 | |||
| url = http://www.fas.org/irp/nsa/spartans/chapter2.pdf }}</ref> | |||
:#Pre-buildup, 1954-1960. | |||
:# The Early Years: 1961-1964, characterized by direction-finding and COMSEC, ending with the Gulf of Tonkin Incident. This partially overlaps the period of "SIGINT and the Attempted Coups against Diem, 1960-1962"<ref name=NSAVN-2 /> | |||
:# The Buildup: 1965-1967, with cooperation at the Corps/Field Force level, and the integration of South Vietnamese linguists. Major ASA units at this time were the 509th Radio Research Group and 403d RR (Radio Research) SOS (Special Operations Detachment)<ref name=Gilbert /> | |||
:#Electronic Warfare: 1968-1970, with substantial technical experimentation | |||
:#Vietnamization: 1971-1973, as the mission shifted back to training, advising, and supporting South Vietnamese units. which do not match the more recent NSA history by Hanyok, which is less focused on events with the US military. <ref name=NSAVN-2 /> | |||
:# The Early Years: 1961-1964, characterized by direction-finding and COMSEC, ending with the Gulf of Tonkin Incident. This partially overlaps the period of "SIGINT and the Attempted Coups against Diem, 1960-1962"<ref name=NSAVN-2 /> | |||
:# The Buildup: 1965-1967, with cooperation at the Corps/Field Force level, and the integration of South Vietnamese linguists. Major ASA units at this time were the 509th Radio Research Group and 403d RR (Radio Research) SOS (Special Operations Detachment)<ref name=Gilbert /> | |||
:#Electronic Warfare: 1968-1970, with substantial technical experimentation | |||
:#Vietnamization: 1971-1973, as the mission shifted back to training, advising, and supporting South Vietnamese units. | |||
Hanyok divides the history into periods based on enemy action, while Gilbert divides it on American deployments and changes in technology.<ref name=NSAVN-3 />US SIGINT support during the Vietnam War came principally from service cryptographic units, with some NSA coordination. Units still belonged to their parent service, such as the [[Army Security Agency]] and [[Naval Security Group]]. Some SIGINT personnel were assigned to covert special operations and intelligence units.Although SIGINT personnel were present in 1960, Gilbert breaks the ASA involvement in Vietnam into four chronological phases,<ref name=Gilbert /> which do not match the more recent NSA history by Hanyok, which is less focused on events with the US military. <ref name=NSAVN-2 /> | |||
Although SIGINT personnel were present in 1960, Gilbert breaks the ASA involvement in Vietnam into four chronological phases,<ref name=Gilbert /> which do not match the more recent NSA history by Hanyok, which is less focused on events with the US military. <ref name=NSAVN-2 /> | |||
:# The Early Years: 1961-1964, characterized by direction-finding and COMSEC, ending with the Gulf of Tonkin Incident. This partially overlaps the period of "SIGINT and the Attempted Coups against Diem, 1960-1962"<ref name=NSAVN-2 /> | :# The Early Years: 1961-1964, characterized by direction-finding and COMSEC, ending with the Gulf of Tonkin Incident. This partially overlaps the period of "SIGINT and the Attempted Coups against Diem, 1960-1962"<ref name=NSAVN-2 /> | ||
:# The Buildup: 1965-1967, with cooperation at the Corps/Field Force level, and the integration of South Vietnamese linguists. Major ASA units at this time were the 509th Radio Research Group and 403d RR (Radio Research) SOS (Special Operations Detachment)<ref name=Gilbert /> | :# The Buildup: 1965-1967, with cooperation at the Corps/Field Force level, and the integration of South Vietnamese linguists. Major ASA units at this time were the 509th Radio Research Group and 403d RR (Radio Research) SOS (Special Operations Detachment)<ref name=Gilbert /> | ||
:#Electronic Warfare: 1968-1970, with substantial technical experimentation | :#Electronic Warfare: 1968-1970, with substantial technical experimentation | ||
:#Vietnamization: 1971-1973, as the mission shifted back to training, advising, and supporting South Vietnamese units. | :#Vietnamization: 1971-1973, as the mission shifted back to training, advising, and supporting South Vietnamese units.<ref name=Gilbert /> | ||
= | |||
The NSA History redacted most information, not already public, from 1954 to 1960, but gaps can be filled from other sources A section is titled "Diem's War against Internal Dissent". It opens with an observation that most opposition to President [[Ngo Dinh Diem| Diem]] was inflamed by "his program of wholesale political suppression, not just of the Viet Minh cadre that had stayed in the south after Geneva, but against all opposition, whether it was communist or not." By mid-1955, according to Diem, approximately 100,000 Communists were alleged to have surrendered, or rallied to Diem, although the NSA author suggests this did not correspond to political reality, since there were only an estimated 10,000 "stay-behinds". It was clear, however, that the number of communists at large dropped dramatically. | |||
The history mentions that Diem's security organs were given a free hand by Ordnance Number 6 of January 1956, putting anyone deemed a threat to the defense of the state and public safety," at least in house arrest. A quote from ''Life'' magazine, generally considered friendly to Diem, suggested that a substantial number of non-communists had been arrested. This is followed by a brief note, "Yet in that same process of neutralizing opposition, Diem set the seeds for his own downfall." This followed by long redactions. Both Diem and the US [[Military Assistance Advisory Group]] (MAAG), according to the NSA history, felt the communists were going into "last gasps" in late 1959.<ref name=NSAVN-2>{{citation | |||
| chapter = Chapter 2 - The Struggle for Heaven's Mandate: SIGINT and the Internal Crisis in South Vietnam, [Deleted] 1962 | |||
| title = Spartans in Darkness: American SIGINT and the Indochina War, 1945-1975 | |||
| first1 = Robert J. | last1 =Hanyok | |||
| publisher = Center for Cryptologic History, National Security Agency | |||
| year = 2002 | |||
| url = http://www.fas.org/irp/nsa/spartans/chapter2.pdf }}</ref> | |||
For the period before large-scale U.S. involvement, see '''[[National Security Agency and Southeast Asia, 1954-1961]]'''. | |||
== | ==NSA and Western Counterespionage== | ||
For several years, "the fact of" the existence of NSA was not acknowledged, and for many years thereafter, one of the Washington area sayings was that the initials stood for "Never Say Anything", and the physical security of the campus was far greater than that at CIA. In spite of that attitude, however, there were several severe security breaches by staff working as Soviet [[counterintelligence#defector in place|defectors in place]], or people who defected with maximum publicity. | |||
NSA also engaged in questionably legal surveillance of civilian international traffic either originating or terminating in the United States. | |||
===Weisband=== | |||
ASA in the post-World War II period had broken messages used by the Soviet armed forces, police and industry, and was building a remarkably complete picture of the Soviet national security posture. It was a situation that compared favorably to the successes of World War II. Then, during 1948, in rapid succession, every one of these cipher systems went dark, as a result of espionage by a Soviet agent, [[William Weisband]]. NSA suggests this may have been the most significant loss in US intelligence history. <ref name=NSA-Korea /> | |||
===Martin and Mitchell=== | |||
William Martin and Bernon Mitchell were NSA mathematicians, regarded highly for their scientific insight, but generally have been accepted to have odd socialization. <ref name=SW2007-07-18>{{Citation | |||
| title The Worst Internal Scandal in NSA History Was Blamed on Cold War Defectors’ Homosexuality: But what if they weren’t gay? | |||
| first = Rick | last = Anderson | |||
| date = July 18, 2007 | |||
| journal = Seattle Weekly | |||
| url =http://www.seattleweekly.com/2007-07-18/news/the-worst-internal-scandal-in-nsa-history-was-blamed-on-cold-war-defectors-homosexuality.php }}</ref> In 1960, they left on vacation, and eventually showed up in a Soviet press conference, speaking of the evils of the NSA. At the time, it was widely rumored that they were homosexual, but new evidence suggests while they may have been social misfits, there is little evidence they were gay. The ''Seattle Times''' obtained files that said | |||
<blockquote>"Beyond any doubt," the unnamed author of a then-secret NSA study on the damage done by the defection wrote in 1963, according to the recently released documents, "no other event has had, or is likely to have in the future, a greater impact on the Agency's security program."</blockquote> | |||
===Dunlop=== | |||
Jack Dunlop was, as a member of the military, a courier and driver for the [[National Security Agency]]. After retirement, he applied for a civilian job at NSA, but the more intensive [[security clearance]] process soon revealed unexplained large income. | |||
=== | He committed suicide before it was fully determined that he was selling documents to the Soviet Union. | ||
===Walker Ring=== | |||
Communications security personnel for the Navy (and Central Security Service), John Walker and a number of family members and friends sold immense amounts of communications security information to the Soviets. The material revealed has often been called the greatest compromise in the history of the United States. He plea-bargained a reduced sentence for his son, but the rest of the ring are lifetime guests of the U.S. [[Bureau of Prisons]]. | |||
===US domestic surveillance=== | |||
During this period, several programs, potentially in violation of its foreign intelligence charter, the NSA (and its AFSA predecessor) monitored international telegram and selected voice communications of American citizens<ref name=SenateNSA75/>.[[Project SHAMROCK]], started during the fifties under AFSA, the predecessor of NSA, and terminated in 1975, was a program in which [[NSA]] obtained copies, without a warrant, of telegrams sent by international record carriers. The related [[Project MINARET]] intercepted voice communications of persons of interest to US security organizations of the time, including Malcolm X, Jane Fonda, Joan Baez, and Martin Luther King. | |||
===Western counterespionage=== | |||
From 1943 to 1980, the [[VENONA]] project, principally a US activity with support from Australia and the UK, recovered information, some tantalizingly only in part, from Soviet espionage traffic. See article on [[VENONA]]. VENONA gave substantial information on the scope of Soviet espionage against the West, but critics claim some messages have been interpreted incorrectly, or are even false. Part of the problem is that certain persons, even in the encrypted traffic, were identified only by code names such as "Quantum". Quantum was a source on US nuclear weapons, and is often considered to be [[Julius and Ethel Rosenberg|Julius Rosenberg]]. The name, however, could refer to any of a number of spies. | |||
==Collection methods advance== | |||
Before satellite SIGINT was practical, US information about Soviet radar stopped about 200 miles inland from the coastline. After these space systems went into service, effectively all radars on the Soviet landmass became known to NSA. They informed the [[Strategic Air Command]] with the technical details and locations of air defense radars, which went into planning attack routes of the [[Single Integrated Operational Plan]] (SIOP), the master set of plans for nuclear warfare. They provided operational information to Navy commanders. Coupled with IMINT from CORONA, they helped CIA, DIA and other elements of the intelligence community understand the overall Soviet threat. | |||
There were still specific cases where aircraft were needed -- and where crews died. UAVs became increasingly more attractive for such high-risk missions. | |||
===Space systems begin=== | |||
The first successful SIGINT satellites, known informally as "Ferrets", were classified payloads aboard the [[Galactic Radiation and Background]] (GRAB), designed by the [[U.S. Naval Research Laboratory]]. GRAB had an unclassified experiment called Solrad, and an [[ELINT]] package called TATTLETALE. See [[National Reconnaissance Office]] (NRO), an agency even more secretive than NSA for more detail on GRAB/TATTLETALE. As the military cryptologic agencies, using ground, sea, and aircraft platforms, actually intercepted and processing raw SIGINT material to be forwarded to Fort Meade, the NRO was responsible for similar capture, but from satellites that NRO was responsible for launching and operating. | |||
According to the NRO, the incremental upgrade of GRAB's Tattletale package was [[Poppy (satellite)| POPPY]]. The second program, Poppy, operated from 1962 to 1977. The "fact of" the Poppy program, along with limited technical information, was declassified in 2004. <ref name=NROperiscope>{{citation | |||
| url = http://thememoryhole.org/nro/nro_raising-periscope.pdf | |||
| last1 = MacDonald | first1= Robert A. | |||
| last2 = Moreno | first1 = Sharon K. | |||
| title = Raising the Periscope... Grab and Poppy, America's early ELINT Satellites | |||
| year = 2005 | |||
| publisher = U.S. National Reconnaissance Office}}</ref> At least three NRO operators did the preliminary processing of the POPPY data, one measuring the orbital elements of the satellite and the selected polarization, while the second operator identified signals of interest. The third operator did more detailed, non-real-time, analysis of the signal, and transmitted information to NSA. | |||
After these space systems went into service, most radars on the Soviet landmass became known to NSA. NSA, in turn, provided the characteristics of the Soviet air defense network to the [[Single Integrated Operational Plan]] (SIOP) staff, and to Navy commanders who would operate in Soviet waters. Coupled with IMINT from CORONA, they helped CIA, DIA and other elements of the intelligence community understand the overall Soviet threat. | |||
The U.S. embarked on a new generation of reconnaissance satellites, Air Force Project WS-117L, approved by President [[Dwight D. Eisenhower]] in 1954. This program was focused on IMINT and MASINT, but some satellites would also carry signal intercept subsystem under Project PIONEER FERRET. <ref name=Andronov1993>{{citation | |||
| title = American Geosynchronous SIGINT Satellites | | title = American Geosynchronous SIGINT Satellites | ||
| url = http://www.globalsecurity.org/space/library/report/1993/androart.htm | | url = http://www.globalsecurity.org/space/library/report/1993/androart.htm | ||
| Line 248: | Line 316: | ||
}}</ref> By 1959, WS-117L had split into three programs: <ref name=>{{citation | }}</ref> By 1959, WS-117L had split into three programs: <ref name=>{{citation | ||
| url = http://www.losangeles.af.mil/shared/media/document/AFD-060912-025.pdf | | url = http://www.losangeles.af.mil/shared/media/document/AFD-060912-025.pdf | ||
| title = Chapter V, Space Systems | |||
| author = U.S. Air Force | | author = U.S. Air Force | ||
}}</ref> The major programs were: | |||
}}</ref> | |||
:#Discoverer, the unclassified name for the [[CORONA]] [[IMINT]] satellite | :#Discoverer, the unclassified name for the [[CORONA]] [[IMINT]] satellite | ||
:#Satellite and Missile Observation System (SAMOS)(IMINT) | :#Satellite and Missile Observation System (SAMOS)(IMINT) | ||
:#Missile Defense Alarm System (MIDAS), a [[Electro-optical MASINT#Space-based Staring Infrared Sensors | nonimaging staring infrared MASINT system]] | :#Missile Defense Alarm System (MIDAS), a [[Electro-optical MASINT#Space-based Staring Infrared Sensors | nonimaging staring infrared MASINT system]] | ||
The first experimental ELINT package would fly aboard a photoreconnaissance satellite, Discoverer-13, in August 1960. Translated from the Russian, it was equipped with "Scotop equipment was intended to record the signals of Soviet radars which were tracking the flight of American space objects." <ref name=Andronov1993 /> | The first experimental ELINT package would fly aboard a photoreconnaissance satellite, Discoverer-13, in August 1960. Translated from the Russian, it was equipped with "Scotop equipment was intended to record the signals of Soviet radars which were tracking the flight of American space objects." <ref name=Andronov1993 /> | ||
Soviet sources state the first specialized ELINT satellites, which received the designation of "Ferret," was begun in the USA in 1962.<ref name=Andronov1993 /> In actuality, the first successful SIGINT satellite was the U.S. Navy's [[Galactic Radiation and Background]] (GRAB), designed by the [[U.S. Naval Research Laboratory]]. GRAB had an unclassified experiment called Solrad, and an [[ELINT]] package called Tattletale. Tattletale was also called Canes; CANES was also the [[National Reconnaissance Office]] (NRO) [[Sensitive compartmented information| sensitive compartmented information]] (SCI) [[code name|codeword]] for the control system overall program. GRAB intercepted radar pulses as they came over the horizon, translated the frequency, and retransmitted each pulse, with no further processing, to ground receiving sites.<ref name=NROperiscope>{{citation | Soviet sources state the first specialized ELINT satellites, which received the designation of "Ferret," was begun in the USA in 1962.<ref name=Andronov1993 /> In actuality, the first successful SIGINT satellite was the U.S. Navy's [[Galactic Radiation and Background]] (GRAB), designed by the [[U.S. Naval Research Laboratory]]. GRAB had an unclassified experiment called Solrad, and an [[ELINT]] package called Tattletale. Tattletale was also called Canes; CANES was also the [[National Reconnaissance Office]] (NRO) [[Sensitive compartmented information| sensitive compartmented information]] (SCI) [[code name|codeword]] for the control system overall program. GRAB intercepted radar pulses as they came over the horizon, translated the frequency, and retransmitted each pulse, with no further processing, to ground receiving sites.<ref name=NROperiscope>{{citation | ||
| url = http://thememoryhole.org/nro/nro_raising-periscope.pdf | | url = http://thememoryhole.org/nro/nro_raising-periscope.pdf | ||
| Line 337: | Line 337: | ||
}}</ref> Again examining space-based SIGINT through Soviet eyes, "The tasks of space-based SIGINT were subdivided into two groups: ELINT against antiaircraft and ABM radars (discovery of their location, operating modes and signal characteristics) and SIGINT against C3 systems. In order to carry out these tasks the US developed ... satellites of two types: | }}</ref> Again examining space-based SIGINT through Soviet eyes, "The tasks of space-based SIGINT were subdivided into two groups: ELINT against antiaircraft and ABM radars (discovery of their location, operating modes and signal characteristics) and SIGINT against C3 systems. In order to carry out these tasks the US developed ... satellites of two types: | ||
:*small ELINT satellites which were launched together with photoreconnaissance satellites into initially low orbits and then raised into a polar working orbit at an altitude of 300 to 800 km using on-board engines | :*small ELINT satellites which were launched together with photoreconnaissance satellites into initially low orbits and then raised into a polar working orbit at an altitude of 300 to 800 km using on-board engines | ||
:*heavy (1 to 2 tonne mass) "SIGINT" (possibly the translator's version of COMINT?) satellites, which were put into orbit at an altitude of around 500 km using a Thor-Agena booster. The Soviet source described the satellites of the late sixties as "Spook Bird" or CANYON <ref name=Andronov1993 />, which was the predecessor to the production | :*heavy (1 to 2 tonne mass) "SIGINT" (possibly the translator's version of COMINT?) satellites, which were put into orbit at an altitude of around 500 km using a Thor-Agena booster. The Soviet source described the satellites of the late sixties as "Spook Bird" or CANYON <ref name=Andronov1993 />, which was the predecessor to the production Rhyolite platforms. This was not completely correct if the Soviets thought these were heavy ELINT satellites; [[Canyon (satellite)| CANYON]] was the first COMINT satellite series, which operated from 1968 to 1977. | ||
According to the NRO, the incremental upgrade of GRAB's Tattletale package was [[Poppy (satellite)| POPPY]]. The second program, Poppy, operated from 1962 to 1977. The "fact of" the Poppy program, along with limited technical information, was declassified in 2004. <ref name=NROperiscope>{{citation | According to the NRO, the incremental upgrade of GRAB's Tattletale package was [[Poppy (satellite)| POPPY]]. The second program, Poppy, operated from 1962 to 1977. The "fact of" the Poppy program, along with limited technical information, was declassified in 2004. <ref name=NROperiscope>{{citation | ||
| Line 345: | Line 345: | ||
| title = Raising the Periscope... Grab and Poppy, America's early ELINT Satellites | | title = Raising the Periscope... Grab and Poppy, America's early ELINT Satellites | ||
| year = 2005 | | year = 2005 | ||
| publisher = U.S. National Reconnaissance Office}}</ref> At least three NRO operators did the preliminary processing of the POPPY data, one measuring the orbital elements of the satellite and the selected polarization, while the second operator identified signals of interest. The third operator did more detailed, non-real-time, analysis of the signal, and transmitted information to NSA. | | publisher = U.S. National Reconnaissance Office}}</ref> At least three NRO operators did the preliminary processing of the POPPY data, one measuring the orbital elements of the satellite and the selected polarization, while the second operator identified signals of interest. The third operator did more detailed, non-real-time, analysis of the signal, and transmitted information to NSA. | ||
In the EC-121 shootdown incident of 15 April 1969, an EC-121M of the U[[.S. Navy]]'s Fleet Airborne Reconnaissance Squadron One (VQ-1) Vietnam, took off on a routine SIGINT patrol under the BEGGAR SHADOW program. North Korean air search radar was monitored by the USAF 6918th Security Squadron in Japan, and Detachment 1 6922nd Security Wing at Osan Air Base in Korea, and the Naval Security Group at [[Kamiseya]], [[Japan]]. The EC-121M was not escorted. When US radar detected the takeoff of North Korean interceptors, and the ASA unit lost touch, ASA called for fighters, but the EC-121M never again appeared on radar. 31 crewmen were lost. | |||
In response to this threat on what had been considered a low-risk mission, Ryan was tasked to develop the AQM-34Q as the SIGINT version of the AQM-34P, with antennas along the fuselage. Underwing fuel tanks were added to this model, and the AQM-34R updated the electronics and had standard underwing tanks.<ref name=RyanDrone>{{cite web | |||
| title = RYAN AQM-34G - R | |||
| url = http://www.spyflight.co.uk/aqm34g.htm | |||
}}</ref> Still, some missions still need to be flown by manned aircraft. | |||
===CIA provides additional collection approaches=== | |||
While the Service Cryptologic Elements (SCE) provided intercepts from ground, air and sea platforms were U.S. overt forces could go, and NRO provided satellite basis, cooperation between NSA and CIA's clandestine operations personnel found ways to emplace, secretly, SIGINT sensors behind the Iron Curtain. | |||
Also in 1962, the Central Intelligence Agency, Deputy Directorate for Research, formally took on ELINT and COMINT responsibilities<ref name=CIA-DDR>{{Citation | |||
| last = Central Intelligence Agency | |||
| title = Deputy Director for Research | |||
| date = May 1998 | |||
| url = http://www.gwu.edu/~nsarchiv/NSAEBB/NSAEBB54/st18.pdf | |||
}}</ref>. "The consolidation of the ELINT program was one of the major goals of the reorganization....it is responsible for: | |||
:*Research, development, testing, and production of ELINT and COMINT collection equipment for all Agency operations. | |||
:*Technical operation and maintenance of CIA deployed non-agent ELINT systems. | |||
:*Training and maintenance of agent ELINT equipments | |||
:*Technical support to the Third Party Agreements. | |||
:*Data reduction of Agency-collected ELINT signals. | |||
:*ELINT support peculiar to the penetration problems associated with the Agent's reconnaissance program under NRO. | |||
:*Maintain a quick reaction capability for ELINT and COMINT equipment." | |||
"CIA's Office of Research and Development was formed to stimulate research and innovation testing leading to the exploitation of non-agent intelligence collection methods....All non-agent technical collection systems will be considered by this office and those appropriate for field deployment will be so deployed. The Agency's missile detection system, Project [deleted] based on backscatter radar is an example. This office will also provide integrated systems analysis of all possible collection methods against the Soviet antiballistic missile program is an example." <ref name=CIA-DDR />. It is not clear where ELINT would end and MASINT would begin for some of these projects, but the role of both is potentially present. MASINT, in any event, was not formalized as a US-defined intelligence discipline until 1986. | |||
===US Submarine SIGINT begins=== | |||
Under the code names HOLYSTONE, PINNACLE, BOLLARD, and BARNACLE, began in 1959, US submarines infiltrated Soviet harbors to tap communications cables and gather SIGINT. They also had a MASINT mission against Soviet submarines and missiles. The program, which went through several generations, ended when compromised, by [[Ronald Pelton]], in 1981.<ref name=Richelson1989>{{Citation | |||
| author = Jeffrey Richelson | |||
| title = The US Intelligence Community, 2nd Edition, Chapter 8, Signals Intelligence | |||
| id = Richelson 1989 | |||
| year = 1989 | |||
| url = http://jya.com/usic08.htm | |||
}}</ref> | |||
===Early UAV development=== | |||
[[Unmanned aerial vehicle]] (UAV), called "drones" at the time, were introduced quite early and served a number of purposes, although SIGINT was not the first mission. <ref name=RyanDrone>{{cite web | |||
| title = RYAN AQM-34G - R | |||
| url = http://www.spyflight.co.uk/aqm34g.htm | |||
}}</ref> won the US Air Force competition for the Q-2 jet-propelled aerial target. Known as the Q-2A Firebee, the jet-propelled UAV, launched by a rocket and recovered by parachute, was also bought by the Navy and Army. | |||
= | In 1961, the Air Force requested a reconnaissance version of what was then designated the BQM-34A, which resulted in the Firebee Model 147A, to be designated the AQM-34.<ref name=RyanDrone /> This UAV looked like its target version, but carried more fuel and had a new navigation system. These reconnaissance drones were air-launched from a D[[C-130]] modified transport. Like all subsequent versions of this UAV, it was air-launched from underneath the wing of a specially modified Lockheed DC-130 Hercules, rather than ground-launched with rocket assistance. These are thought to have been operationally for IMINT, although SIGINT was considered, as more aerial US reconnaissance platforms do SIGINT than IMINT, and most IMINT platforms, such as the [[U-2]] and [[SR-71]] also have SIGINT capability. Drones of this version were to be used in the Cuban Missile Crisis.<ref name=RyanDrone /> | ||
==The Cuban Crisis and the hotter part of the Cold War== | |||
While the start of the [[Cuban Missile Crisis]] came from IMINT showing Soviet missiles under construction, SIGINT had had an earlier role in suggesting that increased surveillance of Cuba might be appropriate. NSA had intercepted suspiciously blank shipping manifests to Cuba, and, through 1961, there was an increasing amount of radio chatter suggestive of Cuba receiving both Soviet weapons and personnel. The weapons could be used offensively as well as defensively<ref name=NSA-Cuba>{{Citation | While the start of the [[Cuban Missile Crisis]] came from IMINT showing Soviet missiles under construction, SIGINT had had an earlier role in suggesting that increased surveillance of Cuba might be appropriate. NSA had intercepted suspiciously blank shipping manifests to Cuba, and, through 1961, there was an increasing amount of radio chatter suggestive of Cuba receiving both Soviet weapons and personnel. The weapons could be used offensively as well as defensively<ref name=NSA-Cuba>{{Citation | ||
| last = Johnson | | last = Johnson | ||
| Line 358: | Line 396: | ||
| title = NSA and the Cuban Missile Crisis | | title = NSA and the Cuban Missile Crisis | ||
| date = May 1998 | | date = May 1998 | ||
| url = http://www.nsa.gov/cuba/}}</ref>. | | url = http://www.nsa.gov/cuba/ | ||
}}</ref>. | |||
In September and October 1962, SIGINT pointed to the completion of a current Soviet air defense network in Cuba, presumably to protect something. The key [[U-2]] flight that spotted the ballistic missiles took place on [[October 15]]. While the IMINT organizations were most critical, an anecdote of the time, told by Juanita Moody, the lead SIGINT specialist for Cuba, that the newly appointed Director of NSA, LTG Gordon Blake, came by to see if he could help. "She asked him to try to get additional staff to meet a sudden need for more personnel. Shortly she heard him on the telephone talking to off-duty employees: "This is Gordon Blake calling for Mrs. Moody. Could you come in to work now?" | In September and October 1962, SIGINT pointed to the completion of a current Soviet air defense network in Cuba, presumably to protect something. The key [[U-2]] flight that spotted the ballistic missiles took place on [[October 15]]. While the IMINT organizations were most critical, an anecdote of the time, told by Juanita Moody, the lead SIGINT specialist for Cuba, that the newly appointed Director of NSA, LTG Gordon Blake, came by to see if he could help. "She asked him to try to get additional staff to meet a sudden need for more personnel. Shortly she heard him on the telephone talking to off-duty employees: "This is Gordon Blake calling for Mrs. Moody. Could you come in to work now?" | ||
| Line 370: | Line 409: | ||
| date = 1995 | | date = 1995 | ||
| url = http://www.coldwar.org/text_files/rb47_rc135.doc | | url = http://www.coldwar.org/text_files/rb47_rc135.doc | ||
}}</ref> | |||
Tactical Naval SIGINT monitored stopped Soviet transports, when it was unknown if they would challenge the naval quarantine. Direction finding confirmed they had turned around. <ref name=NSA-Cuba /> | Tactical Naval SIGINT monitored stopped Soviet transports, when it was unknown if they would challenge the naval quarantine. Direction finding confirmed they had turned around. <ref name=NSA-Cuba /> | ||
While certain drone functions failed in the Cuban crisis, they were soon ready for service. DC-130 launchers and controllers were deployed to Kadena in Okinawa, and the Bien Hoa in Vietnam. The real-time telemetry, hoped for during the Cuban crisis, was now a reality, and RB-47H ELINT aircraft were dedicated to Southeast Asian operations. | |||
RC-135Ms were flying at the same time, but primarily against China and Russia. Eventually, their missions focused on Southeast Asia.<ref name=Bailey1995 /> | |||
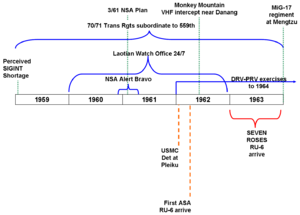
==US-RVN doctrine, 1961== | |||
In January 1961, while the Vietnam embassy and military group prepared a counterinsurgency plan, the SIGINT community did its own planning. The first review of the situation assumed limited support to the ARVN COMINT teams. Essentially, the policy was that the South Vietnamese would be trained in basic direction finding using "known or derived" technical information, but, for security reasons, COMINT that involved more sophisticated analysis would not be shared. It was also felt that for at least the near term, ARVN COMINT could not provide meaningful support, and the question was presented, to the State Department, if it was politically feasible to have US direction-finding teams operate inside South Vietnam. The March 1961 plan included both tactical support and a strategic COMINT mission collection NVA data for NSA. | In January 1961, while the Vietnam embassy and military group prepared a counterinsurgency plan, the SIGINT community did its own planning. The first review of the situation assumed limited support to the ARVN COMINT teams. Essentially, the policy was that the South Vietnamese would be trained in basic direction finding using "known or derived" technical information, but, for security reasons, COMINT that involved more sophisticated analysis would not be shared. It was also felt that for at least the near term, ARVN COMINT could not provide meaningful support, and the question was presented, to the State Department, if it was politically feasible to have US direction-finding teams operate inside South Vietnam. The March 1961 plan included both tactical support and a strategic COMINT mission collection NVA data for NSA. | ||
| Line 445: | Line 431: | ||
| title = Army Security Agency | | title = Army Security Agency | ||
| url = http://www.espionageinfo.com/An-Ba/Army-Security-Agency.html | | url = http://www.espionageinfo.com/An-Ba/Army-Security-Agency.html | ||
}}</ref>. | |||
==Drones evolve(1967-1971) == | |||
A major advance for high-risk IMINT and SIGINT missions was the high-altitude AQM-34N<ref name=RyanDrone /> COMPASS DAWN, which flew as high as 70000 ft and had a range over 2,400 miles. AQM-34N's flew 138 missions between March 1967 and July 1971, and 67% were parachute-recovered with the new Mid-Air Retrieval System, which used a helicopter to grab the parachute cable in mid-air. While this had an [[IMINT]] mission, the potential of high altitude for SIGINT over a wide area was obvious. | |||
In the [[EC-121 shootdown incident]] of 15 April 1969 , an EC-121M of the U.S. Navy's Fleet Airborne Reconnaissance Squadron One (VQ-1) Vietnam, took off on a routine SIGINT patrol under the BEGGAR SHADOW program. North Korean air search radar was monitored by the USAF 6918th Security Squadron in Japan, and Detachment 1 6922nd Security Wing at Osan Air Base in Korea, and the Naval Security Group at Kamiseya, Japan. The EC-121M was not escorted. When US radar detected the takeoff of North Korean interceptors, and the ASA unit lost touch, ASA called for fighters, but the EC-121M never again appeared on radar. 31 crewmen were lost. | |||
In response to this threat on what had been considered a low-risk mission, Ryan was tasked to develop the AQM-34Q was the SIGINT version of the AQM-34P, with antennas along the fuselage. Underwing fuel tanks were added to this model, and the AQM-34R updated the electronics and had standard underwing tanks.<ref name=RyanDrone /> | |||
: | ==1980s== | ||
: | ===Strategic SIGINT satellites for NSA=== | ||
: | |||
From 1972 to 1989, low earth orbit SIGINT satellites were launched only as secondary payloads with [[KH-9]] and [[KH-11]] IMINT satellites. They were code-named after female sex symbols, such as RAQUEL, FARRAH, BRIDGET and MARILYN.<ref name=Richelson1989 /> | |||
===== | |||
Four geosynchronous RHYOLITE satellites were launched in the seventies, with COMINT and TELINT missions.<ref name=EArhyolite>{{citation | |||
| title =Encyclopedia Astronautica | |||
| chapter = Rhyolite | |||
| url = http://www.astronautix.com/craft/rhyolite.htm | |||
}}</ref> These were reported to be directed against line-of-sight microwave, telemetry, or both. Their signals downlinked to Pine Gap station in Alice Springs, Australia. According to ''Encyclopedia Astronautica'', the downlink was in a remote location, to prevent Soviet or Chinese SIGINT personnel from intercepting the downlink, and, in turn, discovering the targeting of the satellites. Downlinked data was then encrypted and retransmitted to NSA at Fort Meade, MD. | |||
The project became unusually public as it was the key element in the espionage trial of the 'Falcon and the Snowman', Boyce and Lee. Rhyolite was also known as Program 720, Program 472, and Aquacade. After having the name compromised when [[Christopher Boyce]] sold information to the Soviets, the code name was changed to AQUACADE. In the late seventies, another class of geosynchronous SIGINT satellites, first called CHALET and renamed VORTEX after the code name was compromised. After the loss of Iranian monitoring stations, these satellites were also given an TELINT capability.<ref name=Richelson1989 /> | |||
JUMPSEAT ELINT satellites, using a Moliyna orbit, started launching in 1975.<ref name=Richelson1989 /> Their launch parameters were very similar to the SDS communications satellites used for connectivity in high latitudes, and individual launches could easily have been either JUMPSEAT or SDS.<ref name=EAjumpseat>{{citation | |||
| title =Encyclopedia Astronautica | |||
| chapter = Jumpseat | |||
| url = http://www.astronautix.com/craft/rhyolite.htm | |||
}}</ref> While the primary mission of JUMPSEAT constellations appeared to be microwave COMINT, they may also have had ELINT capabilities. | |||
==1980s== | |||
This was a decade of world change, with changes in Cold War emphasis and alliances, the first submarine attack since World War II in the context of a regional war involving extensive power projection, low- and medium-intensity operations, and continuing national policy development. | |||
===1980s Cold War SIGINT=== | |||
Roughly from the late 1980s on, there was cooperation between the US and the PRC in collecting SIGINT of mutual interest, principally against Russia <ref>{{Citation | |||
| last = Association of Former Intelligence Officers | |||
| title = China SIGINT Capabilities | |||
| work = Weekly Intelligence Notes #15-01 | |||
| id = ChineseSIGINT | |||
| date = 16 April 2001]] | |||
| year = | |||
| url = http://www.afio.org/sections/wins/2001/2001-15.html | |||
}}</ref>. It is believed that the Qitai and Korla sites, in Xinjiang (Sinkiang) are operated jointly by the Chinese and the US CIA Office of SIGINT Operations against Soviet missile tests and space launches, but their current status is uncertain. It is also unclear if the Office of SIGINT Operations is still part of CIA, or if NSA may operate these sites. | |||
Spruance-class destroyers sailed on collection missions in the Black Sea, Baltic Sea, and off the coast of Libya, a Soviet client.<ref name=Richelson1989 /> | |||
===1980s Falklands War SIGINT=== | |||
Under the UKUSA Agreement, Great Britain called upon NSA SIGINT satellite resources to collect relevant information. Tension existed because the controversial British investigative journalist, Duncan Campbell, had published information considered sensitive. According to one former British SIGINT officer, "We can ask the Americans to do things, but we cannot compel them. There may be targets they don't want to cover. The Falklands was a factor here. It brought going it alone back into fashion."<ref name=Urban1996>{{Citation | |||
| author = Mark Urban | |||
| title = UK Eyes Alpha: the Inside Story of British Intelligence. Chapter 5: Zircon | |||
| id = Urban 1996 | |||
| url = http://www.fas.org/irp/eprint/alpha/zircon.htm | |||
}}</ref> | |||
===1980s strategic SIGINT policy=== | |||
In 1980, U.S. intercepts of Soviet communications generated a fear that the Soviets were about to invade Iran. In 1983 intercepts allowed the United States to piece together the details concerning the sinking of a Soviet submarine in the North Pacific. | |||
In 1983 it began an all-source program targeting Soviet prison camp system, with the specific intent of issuing a study that would embarrass the Soviets<ref name=Richelson1989/>. | |||
MAGNUM geosynchronous SIGINT satellites were first launched from the Space Shuttle in 1985. These were believed to be more sensitive and perhaps stealthier than RHYOLITE/AQUACADE. | |||
After the Liberty and Pueblo incidents, only combatant ships, destroyers and frigates, were used for collection missions. In addition to SIGINT intercept against the Soviets, combatant ships operated off Nicaragua, El Salvador, and Honduras. One purpose-built SIGINT auxiliary, the ARL-24 ''Sphinx'', generally stayed off the Nicaraguan coast. | |||
==1990s== | |||
Terrorism from foreign groups became an increasingly major concern, as with the 1992 al-Qaeda attack in Yemen, the 1993 truck bombing of the World Trade Center, 1995 (Saudi communications center) and 1996 (Khobar Towers) in Saudi Arabia, and the 1998 bombings of the US embassies in Dar es Salaam, Tanzania and Nairobi, Kenya. Third world and non-national groups, with modern communications technology, in many ways are a harder SIGINT target than a nation, such as Russia or China, that sends out large amounts of traffic. According to the retired Commandant of the US Marines, [[Alfred M. Gray, Jr.]], some of the significant concerns of these targets are: | |||
:*Inherently low probability of intercept/detection (LPI/LPD) because off-the-shelf radios can be frequency agile, spread spectrum, and transmit in bursts. | |||
:*Additional frequencies, not normally monitored, can be used. These include citizens band, marine (MF, HF, VHF) bands, and higher frequencies for short-range communications | |||
:*Extensive use of telephones, almost always digital. Cellular and satellite telephones, while wireless, are challenging to intercept, as is Voice over IP (VoIP) | |||
:*Commercial strong encryption for voice and data | |||
:*"Extremely wide variety and complexity of potential targets, creating a "needle in the haystack" problem" <ref>{{cite journal | |||
| last = Gray | |||
| first = Alfred M. | |||
| title = Global Intelligence Challenges in the 1990s | |||
| journal = American Intelligence Journal | |||
| pages = 37-41 | |||
| date = Winter 1989- 1990 | |||
| url = http://www.oss.net/dynamaster/file_archive/041103/e0bf2d2f6a4730a0845a01de675660f5/USMC-1993-07%20General%20Al%20Gray%20on%20Global%20Intelligence%20Challenges.pdf | |||
}}</ref> | |||
==2000s== | |||
As evidenced by the [[Hainan Island incident]], even while China and the US may cooperate on matters of mutual concern towards Russia, the Cold War has not completely disappeared. | |||
There was more regional cooperation, often driven by concerns about transnational terrorism. European countries also are finding that by sharing the cost, they can acquire SIGINT, IMINT, and MASINT capabilities independent of the US. | |||
In the US, both communications security and COMINT policies have been evolving, some with challenges. The adoption of a Belgian-developed [[encryption]] algorithm, approved in a public process, and accepted both for sensitive but unclassified traffic, as well as for classified information sent with NSA-generated and maintained keys, redraws the cryptologic environment as no longer NSA or not-NSA. Controversy continues on various types of COMINT justified as not requiring warrants, under the wartime authority of the President of the United States. | |||
Technologically, there was much greater use of [[Unmanned aerial vehicle|UAVs]] as SIGINT collection platforms. | |||
===Hainan Island incident=== | |||
In 2001, a US EP-3 SIGINT aircraft had a midair collision with a shadowing Chinese fighter, in what has become known as the [[Hainan Island incident]]. Both sides blamed the other, although the US claimed the aircraft was in international airspace, a reasonable assumption given the amount of navigational instrumentation it carries. The fighter pilot died, and the EP-3 made an emergency landing in China, erasing as much sensitive information as possible. While the Chinese did not release the aircraft for several months, the crew having been released earlier, the most sensitive information was not so much the aircraft's instrumentation, but the signals it was targeting and the reference material about the Chinese "electronic order of battle". | |||
===Cryptologic expertise outside NSA=== | |||
The US government withdrew the last approvals for the [[Data Encryption Standard]], approved for unclassified use in 1976 but now considered quite vulnerable. Its replacement, the [[Advanced Encryption Standard]] (AES) was approved in 2002. AES, when used with NSA-supplied keys, is approved for TOP SECRET traffic as well as unclassified, and may be considered a reference point for strong commercial encryption. AES appears, at the present time, to be secure when used properly, which represents a major change in US policy about the availability of strong communications security. Not all governments will allow the use of such strong ciphers. | |||
That the algorithm chosen came from Europe points to a more multilateral world with respect to communications security. AES was developed by two Belgian cryptographers, Joan Daemen and Vincent Rijmen, and submitted to the [[AES competition|AES selection process]] under the name "Rijndael", a portmanteau of the names of the inventors. | |||
===Terrorism and response in the US=== | |||
As a result of the 9/11 attacks, intensification of US intelligence efforts, domestic and foreign, were to be expected. A key question, of course, was whether US intelligence could have prevented or mitigated the attacks, and how it might prevent future attacks. It should be noncontroversial that there will be a delicate balance of intelligence and civil liberties issues. | |||
====SIGINT and the 9/11 attacks==== | |||
In a statement to a joint meeting of the House and Senate Intelligence Committees, NSA Director LTG [[Michael Hayden]] said "NSA had no SIGINT suggesting that al-Qa'ida was specifically targeting New York and Washington, D.C., or even that it was planning an attack on U.S. soil. Indeed, NSA had no knowledge before 9/11 that any of the attackers were in the United States.... | |||
"We are digging out of a deep hole. NSA downsized about one-third of its manpower and about the same proportion of its budget in the decade of the 1990s. That is the same decade when packetized communications (the e-communications we have all become familiar with) surpassed traditional communications. That is the same decade when mobile cell phones increased from 16 million to 741 million an increase of nearly 50 times. That is the same decade when Internet users went from about 4 million to 361 million an increase of over 90 times. Half as many landlines were laid in the last six years of the 1990s as in the whole previous history of the world. In that same decade of the 1990s, international telephone traffic went from 38 billion minutes to over 100 billion. This year, the world's population will spend over 180 billion minutes on the phone in international calls alone. | |||
"throughout the summer of 2001 we had more than 30 warnings that something was imminent. We dutifully reported these, yet none of these subsequently correlated with terrorist attacks. The concept of "imminent" to our adversaries is relative; it can mean soon or imply sometime in the future"<ref name=Hayden2002>{{Citation | |||
| last = Joint Hearings of the US House and Senate Intelligence Committees | |||
| title = Statement of LTG Michael V. Hayden, Director, National Security Agency | |||
| date = 17 October 2002 | |||
| year = 2002 | |||
| url = http://www.fas.org/irp/congress/2002_hr/101702hayden.html | |||
}}</ref> | |||
==References== | ==References== | ||
{{reflist|2}} | {{reflist|2}}[[Category:Suggestion Bot Tag]] | ||
Latest revision as of 06:00, 24 September 2024
The National Security Agency (NSA), formally the National Security Agency/Central Security Service, is part of the U.S. Department of Defense and also the U.S. intelligence community . Its headquarters are at Fort Meade, Maryland, although it has worldwide installations.
The headquarters, which consists of several large buildings, an impressive fence, and acres of parking lots, is reputed to have the most computers of any place on earth.
In its name, national security was selected as deliberately vague and euphemistic; the very existence of the organization was originally classified. It has dual responsibilities:
- As a member of the United States intelligence community , it has the principal responsibility for collecting and processing signals intelligence.
- As the agency responsible for the "Information Assurance mission [to provide] the solutions, products, and services, and [conduct] defensive information operations, to achieve information assurance for information infrastructures critical to U.S. national security interests"[1] The abbreviation "NSA" is not infrequently and facetiously explained as "no such agency" or "never say anything". In fact, there have even been more secret intelligence organizations; the "fact of" the existence of the National Reconnaissance Office (NRO) remained classified for many more years. Smaller organizations, such as the U.S. Special Operations Command organization originally called the Intelligence Support Agency, is reported to change its classified English-language name every two years, and the code word for it every six months — or immediately if the code becomes public.
Immediately outside one of the security gates is the National Cryptologic Museum and the National Vigilance Park, the latter holding three aircraft, one from each service, and of a type that was lost during SIGINT operations.
SIGINT personnel not only died on duty in aircraft. The first U.S. soldier killed in Vietnam belonged to an Army SIGINT unit. A large number of personnel were killed in the Israeli attack on the SIGINT ship, USS Liberty.
Organization
NSA has several kinds of organizational relationships. It has its own leadership, its specific relation to military organizations through its Central Security Service authority, to the United States intelligence community (IC), certain foreign countries, and participation and education in technologies relevant to its work.
Executive structure
The Director, National Security Agency(DIRNSA)/Chief, Central Security Service is an active-duty, three- or four-star officer from one of the military services. The Deputy Director, National Security Agency is a career civilian. Two senior officials are the Signals Intelligence Director (SID) and the Information Assurance Director (IAD). There are usually some very senior staff specialists bearing titles such as Chief Cryptologist.
Keith B. Alexander, serving as DIRNSA as a lieutenant general, U.S. Army, was nominated for promotion to full general in October 2009.
NSA and the U.S. intelligence community
As mentioned, NSA is part of the United States intelligence community .
NSA also is the lead agency for Operations Security (OPSEC), a counterintelligence function within government that goes beyond communications security.
International
NSA and its predecessors have had a very close relationship with its British Counterpart, the Government Communications Headquarters (GCHQ). The resident U.S. representative there, the Senior U.S. Liaison Officer (SUSLO) holds what is considered a key position. There are also significant liaison relationships with Australia, Canada, and New Zealand, as well as with alliances such as NATO. With increasingly diverse membership in organizations such as NATO, there are increasing problems as to the extent of classified information, especially in a compartmented control system, as used for intelligence and communications security information.
Internal organization
While the exact organization is classified, and has varied over time, it will generally contain functions including:
- National level SIGINT-collection management and operations
- Coordination of tactical SIGINT
- Advanced research and development. NSA is reputed to be the world's largest employer of mathematicians.
- Computing and telecommunications services, usually including research
- Computing and communications security doctrine and education available to non-military, non-intelligence agencies of government, and frequently to the public. Unclassified security work in this area is often joint with the National Institutes for Standards and Technology
- SIGINT processing organizations, generally organized on a regional basis depending on national priorities. NSA is not considered to be an analytic agency that produces "finished intelligence", although, by all indications, it will report on the patterns of COMINT and ELINT information, rather than the content, for example, of messages read through COMINT.
- Defensive information operations, including creating, either in-house or on contract, U.S. COMSEC equipment for classified communications, and cryptographic keying material for classified and certain other types of sensitive but unclassified government communications.
Legal authority
Originally created by Executive Order as a result of a National Security Council directive, NSA is routinely funded in the classified IC budget appropriated by the Congress and signed by the President.
Authority with respect to U.S. citizens
In general, NSA is not intended to participate in domestic law enforcement, or in domestic investigation except for its own personnel security clearances and similar purposes. It has tended to operate more under IC and U.S. Communications Security Board regulations than under explicit legislation.
1950s programs
During this period, several programs, potentially in violation of its foreign intelligence charter, the NSA (and its AFSA predecessor) monitored international telegram and selected voice communications of American citizens[2].Project SHAMROCK, started during the fifties under AFSA, the predecessor of NSA, and terminated in 1975, was a program in which NSA obtained copies, without a warrant, of telegrams sent by international record carriers. The related Project MINARET intercepted voice communications of persons of interest to US security organizations of the time, including Malcolm X, Jane Fonda, Joan Baez, and Martin Luther King.
Programs terminated in the 1970s
US domestic surveillance by NSA
A Senate Select Committee, generally called the Church Committee, began some of the first public hearings on US intelligence. These hearings revealed information that was questionably legal, and led to the termination of some programs, such as Project SHAMROCK and Project MINARET, as well as enacting, in 1978, the Foreign Intelligence Surveillance Act (FISA). FISA established guidelines for COMINT involving US citizens, and established a special FISA Court to approve warrants. The FISA judges were cleared for all intelligence information relevant to warrant requests.
During these hearings, the Director of NSA, LTG Lew Allen, discussed targeting of information, including the names of American citizens, in watch lists: "The use of lists of words, including individual names, subjects, locations, et cetera, has long been one of the methods used to sort out information of foreign intelligence value from that which is not of interest. In the past such lists have been referred to occasionally as watch lists, because the lists were used as an aid to watch for foreign activity of reportable intelligence interest. However, these lists generally did not contain names of U.S. citizens or organizations. The activity in question is one in which U.S. names were used systematically as a basis for selecting messages, including some between U.S. citizens, when one of the communicants was at a foreign location."
Richard M. Nixon ordered the CIA to gather information on foreign sources of controlled substances and how they entered the US. As part of this initiative, the Bureau of Narcotics and Dangerous Drugs (BNDD) requested NSA COMINT related to foreign drug traffic, including watch lists with some U.S. names. International drug trafficking became a formal US Intelligence Board (USIB) requirement in 1971. Other target names for watch lists, concerned with North Vietnam, came from the Defense Intelligence Agency.
During the hearings, LTG Allen said he had received a letter, on October 1, 1973, from Attorney General Elliot Richardson "indicating that he was concerned with respect to the propriety of requests for information concerning U.S. citizens which NSA had received from the FBI and Secret Service. He wrote the following:
"Until I am able more carefully to assess the effect of Keith and other Supreme Court decisions concerning electronic surveillance upon your current practice of disseminating to the FBI and Secret Service information acquired by you through electronic devices pursuant to requests from the FBI and Secret Service, it is requested that you immediately curtail the further dissemination of such information to these agencies." [2]
1990s policy
For a number of years, United States Signals Intelligence Directive (USSID) 18[3] was the policy document governing its interception of the communications of U.S. citizens. This document, which has largely been declassified, may no longer be the primary guidance, as there are controversial claims, by the George W. Bush Administration, of an inherent Presidential authority for warrantless surveillance as part of the national security.
Other relevant regulations come from the Department of Defense [4] and the Department of Justice [5]
It is possible to obtain warrants for interception of communications, by divulging all probable cause to a judge of the Foreign Intelligence Surveillance Court (FISC), who is cleared for all classified information. The FISC is authorized by the Foreign Intelligence Surveillance Act of 1978.
Recent US domestic surveillance issues
Under the George W. Bush administration, there has been a large-scale and controversial capture and analysis of domestic and international telephone calls, claimed to be targeted against terrorism. It is generally accepted that warrants have not been obtained for this activity, sometimes called Room 641A after a location, in San Francisco, where AT&T provides NSA access. While very little is known about this system, it may be focused more on the signaling channel and Call detail records than the actual content of conversations.
Another possibility is the use of software tools that do high-performance deep packet inspection. According to the marketing VP of Narus, "Narus has little control over how its products are used after they're sold. For example, although its lawful-intercept application has a sophisticated system for making sure the surveillance complies with the terms of a warrant, it's up to the operator whether to type those terms into the system...
"That legal eavesdropping application was launched in February 2005, well after whistle-blower Klein allegedly learned that AT&T was installing Narus boxes in secure, NSA-controlled rooms in switching centers around the country. But that doesn't mean the government couldn't write its own code to do the dirty work. Narus even offers software-development kits to customers ".[6] The same type of tools with legitimate ISP security applications also have COMINT interception and analysis capability.
Former AT&T technician Mark Klein, who revealed AT&T was giving NSA access, said in a statement, said a Narus STA 6400 was in the NSA room to which AT&T allegedly copied traffic. The Narus device was "known to be used particularly by government intelligence agencies because of its ability to sift through large amounts of data looking for preprogrammed targets."[6]
In 2006 the Electronic Frontier Foundation (EFF) brought a class action suit, Hepting v. AT&T, against AT&T for allegedly illegally assisting the NSA in a massive program of warrantless wiretaps. Much of their evidence came from Klein. An EFF web page has extensive information, including court documents. Quoting that page: "By providing the NSA with unfettered access to their telecommunications infrastructure — all without warrants or legal order -- AT&T is guilty of violating the Foreign Intelligence Surveillance Act (FISA) as well as the Fourth Amendment".
In June 2008, Congress passed the FISA Amendments Act (FAA), retroactively granting AT&T and other telecommunications companies immunity from prosecution in such cases. As of late 2008, the EFF is both lobbying Congress to rescind that act and challenging it in court as unconstitutional. They have also filed another suit, Jewel vs NSA, this time directly against NSA with George Bush, Dick Cheney and others as co-defendants. Again, they have a web page with information including court documents.
Creation of NSA
- See also: SIGINT in the Second World War
During the Second World War, the Army and Navy had separate signals intelligence and communications security organization, which coordinated only informally. Depending on the service, tactical SIGINT, cryptologic development, strategic SIGINT, and cryptologic operations might be performed by autonomous organizations within a service department.
After the end of World War II, all the Western allies began a rapid drawdown. At the end of WWII, the US still had a COMINT organization split between the Army and Navy. See SIGINT from 1945 to 1989 [7] A 1946 plan listed Russia, China, and a [redacted] country as high-priority targets. This would have long-term implications for Korea and Vietnam.
The Army and Navy formed a "Joint Operating Plan" to cover 1946-1949, but this had its disadvantages. The situation became a good deal more complex with the passage of the National Security Act of 1947, which created a separate Air Force and Central Intelligence Agency, as well as unifying the military services under a Secretary of Defense. While the CIA remained primarily a consumer, the Air Force wanted its own SIGINT organization, responsive to its tactical and strategic needs, just as the Army and Navy often placed their needs beyond that of national intelligence.[8] The Army Security Agency (ASA) had shared the national COMINT mission with the Navy's Communications Supplementary Activity (COMMSUPACT) - which became the Naval Security Group in June 1950. During and after World War II, a portion of Army COMINT assets was dedicated to support of the U.S. Army Air Corps, and, when the independent Air Force was created in 1947, these cryptologic assets were resubordinated to the new organization as the Air Force Security Service (AFSS).
U.S. Secretary of Defense James Forrestal rejected the early service COMINT unification plans. The Department of State objected to the next draft, which put the Central Intelligence Group/Central Intelligence Agency in charge of national COMINT. As a compromise and to centralize common services, the Armed Forces Security Agency (AFSA), was formed by secret executive order in 1948. As opposed to NSA, AFSA did not have the authority for central control of individual service COMINT and COMSEC. Policy direction of COMINT came from the U.S. Communications Intelligence Board (USCIB) which, in April 1949, requested $22 million in funds, including 1,410 additional civilian employees, to expand the COMINT effort.
UKUSA Agreement
While the details remain classified, there is a very high amount of signals intelligence cooperation among the five nations under a 1948 agreement, generally called the UKUSA Agreement
| Country | Agency |
|---|---|
| Australia | Defence Signals Directorate |
| Canada | Communications Security Establishment |
| New Zealand | Government Communications Security Bureau (GCSB) |
| United Kingdom | Government Communications Headquarters (GCHQ) |
| United States | National Security Agency |
Since the geographic location of individual nations make them the optimal place to intercept signals from various worldwide targets, there is a considerable effort to distribute the interception workload and avoid duplication. The five countries appear to have near-total access to the others' raw intercepts and processed SIGINT, but not as much sharing of all-source finished intelligence. Even for finished intelligence, however, there is much exchange. For the Pacific, the USCIB targeted China, and Russia in both the European and Pacific theaters, but Korea was a low-priority target. [9] Korean coverage was incidental to Soviet and Chinese interests in the Korean Peninsula.[9] Both the surprise attack, and the difficulty of rapidly enlarging the SIGINT organization, showed that the organization was imperfect. See Intelligence on the Korean War
NSA created, but the services roll on
President Harry Truman, on 24 October 1952, issued a directive that set the stage for the National Security Agency, whose scope went beyond the pure military. NSA was created on 4 November 1952.[8]
The Service Cryptologic Agencies still had their own identity, even after the formation of NSA. They continued reorganizations independently of NSA; in 1955, ASA took over electronic intelligence (ELINT) and electronic warfare functions previously carried out by the Signal Corps. Since its mission was no longer exclusively identified with intelligence and security, ASA was withdrawn from G-2 control and resubordinated to the Army Chief of Staff as a field operating agency.
Eventually, the individual service SIGINT organizations were to become Service Cryptologic Elements (SCE), with dual reporting to their local operational commands and to NSA/CSS -- and sometimes very little to the local command. The captain of the USS Pueblo, a SIGINT ship, was discouraged from entering the SIGINT compartments of the ship. Pilots of SIGINT aircraft were told where to fly, but were not informed, in detail, what the technicians on board were doing -- unless the technicians issued an urgent warning of a hostile aircraft coming close. Several U.S. SIGINT aircraft were damaged or destroyed.
While the names were to continue to change, the main SCEs reorganized into units principally serving NSA's national-level goals, although there were also tactical SIGINT units within a dual chain of command. Since most NSA system was under compartmented control systems, local military commanders might not have the appropriate clearance. The phrase "behind the green door", from a song and a pornographic movie, became the euphemism for the [[Sensitive compartment information facility}sensitive compartment information facilities (SCIF), behind whose locked and guarded doors the actual SIGINT was done.
| Service | SCE |
|---|---|
| Army | Army Security Agency |
| Navy | Naval Security Group (Marine Radio Battalions were primarily tactical) |
| Air Force | Air Force Security Service |
Coordinating the SCEs
A separate SIGINT and communications security organization, or Service Cryptologic Element (SCE), existed for the US Army, Navy, and Air Force. Some of the differences were quite appropriate to support of the military operations of the particular service; the Air Force would be interested ELINT about air defense radars that a bomber might take in attacking the Soviet Union over a polar route, while the Navy would be more interested in coastal air defense radars. The Army would want to be able to recognize hostile artillery fire control radars, and also how to do tactical direction finding, traffic analysis, and field-level cryptanalysis against opposing ground forces.
All of these services also had capabilities to provide national-level intelligence more appropriate for NSA's mission than for support to military operation. The Army had both fixed and mobile intercept equipment appropriate for long-term listening to ground stations, while the Air Force and Navy could probe new foreign electronic systems as part of national-level intelligence goals.
Even though NSA proper had been formed in 1952, the activities of the Service Cryptologic Agencies were not well coordinated. The Air Force and Navy, for example, might duplicate efforts in probing North Korean radars. Air Force RIVET JOINT RC-135 aircraft collected COMINT of interest to all the services. Navy P2 and P3 electronic capabilities also collected data of relevance to the military as a whole.
Bamford described the first effort to organize the SCEs was to create a "fourth branch" of the military, which triggered intense bureaucratic resistance from the services. A compromise was reached by creating the Central Security Service (CSS). The Director of the NSA (DIRNSA) acquired a "second hat" as the commander of CSS. Just as the services rotated the DIRNSA assignment among their three-star (or three-star eligible) intelligence officers, the actual chief of CSS, reporting to DIRNSA, was a two-star post that also rotated among the services. [10] Bamford describes CSS in different ways. At one point, he speaks of "a former senior NSA official who described it as 'a half-assed, last-minute job' designed to destroy the original fourth-service proposal." Later in the same book, however, draws attention, however, to the almost unparalleled power vested in the DIRNSA through NSCID No. 6, revised on 17 February 1972, "All instructions issued by the Director under the authority provided in this paragraph shall be mandatory, subject only to appeal to the Secretary of Defense." Thus, the DIRNSA is able to bypass "not only the Joint Chiefs, but even the secretaries of the branches" giving him his own SIGINT Army, Navy, Air Force, and Marines.
The idea of a fourth service branch for SIGINT is not unheard of; "NSA’s Canadian cousin, the Communications Security Establishment (CSE) relies entirely upon the Canadian Forces Supplementary Radio System (CFSRS) for all raw SIGINT collection. CFSRS has been a part of the Canadian Forces Information Operations Group (CFIOG) since the latter was established 08 May 1998."[11] Clive uses the example of the Navy SCE, as of 2002, as showing the significance of organizations under CSS control: "the Naval Security Group (NSG) might be the best indicator of the significance of the military contribution to NSA’s SIGINT efforts. According to Steven Aftergood of the Federation of American Scientists (FAS), the NSG is responsible for "Signals Security matters and, for Data Link Vulnerability Assessment Methodology within the Navy Vulnerability Assessment Program." The Naval Security Group Command (NSGC) "coordinates with, tasks as appropriate, and appraises the efforts of commands and offices of the Department of the Navy and NSA/Central Security Service in the fulfillment of Navy logistics support requirements, as directed by the Secretary of Defense. It also participates in NSA studies as required." The cryptologic staff "work with some of the most sophisticated and complex systems the Navy has to offer in performance of their mission." NSGC’s Commander "reports to the Chief, Central Security Service (CSS) as the Navy Element Commander of the CSS and performs cryptologic functions at the National level as the Commander of the Navy's Service Cryptologic Element (SCE)." Considering just NSG’s structure, naval SIGINT, and by inference all military SIGINT, does not appear to be a mainly nominal entity. Certainly, with the information overload that the Internet has brought, even for NSA, they can use all the help they can get."
1950-1954: Strategic SIGINT
In the fifties, only aircraft platforms could obtain SIGINT over the USSR.
In Indochina , the French had a number of direction-finding stations, with about 40 technicians. They monitored Viet Minh, Nationalist and Communist Chinese, British, Dutch and Indonesian communications[7] In general, however, SIGINT in French Indochina was limited by the availability of linguists. [12]
There are several ways to split US SIGINT regarding Southeast Asia into periods. In this article, the emphasis is on strategic systems; see SIGINT from 1945 to 1989 for both tactical details and more information on strategic operations. Gilbert's four periods are focused on the deployment of American units.[13] In contrast, Hanyok's periods [14], although the redactions make it difficult to see exactly why he created chapters as he did, but it would appear that he ties them more to VC/NVA activities, as well as RVN politics, than the US view.
Although SIGINT personnel were present in 1960, Gilbert breaks the ASA involvement in Vietnam into four chronological phases, Although SIGINT personnel were present in 1960, Gilbert breaks the ASA involvement in Vietnam into four chronological phases,[13] which do not match the more recent NSA history by Hanyok, which is less focused on events with the US military. [15]
- Pre-buildup, 1954-1960.
- The Early Years: 1961-1964, characterized by direction-finding and COMSEC, ending with the Gulf of Tonkin Incident. This partially overlaps the period of "SIGINT and the Attempted Coups against Diem, 1960-1962"[15]
- The Buildup: 1965-1967, with cooperation at the Corps/Field Force level, and the integration of South Vietnamese linguists. Major ASA units at this time were the 509th Radio Research Group and 403d RR (Radio Research) SOS (Special Operations Detachment)[13]
- Electronic Warfare: 1968-1970, with substantial technical experimentation
- Vietnamization: 1971-1973, as the mission shifted back to training, advising, and supporting South Vietnamese units. which do not match the more recent NSA history by Hanyok, which is less focused on events with the US military. [15]
- The Early Years: 1961-1964, characterized by direction-finding and COMSEC, ending with the Gulf of Tonkin Incident. This partially overlaps the period of "SIGINT and the Attempted Coups against Diem, 1960-1962"[15]
- The Buildup: 1965-1967, with cooperation at the Corps/Field Force level, and the integration of South Vietnamese linguists. Major ASA units at this time were the 509th Radio Research Group and 403d RR (Radio Research) SOS (Special Operations Detachment)[13]
- Electronic Warfare: 1968-1970, with substantial technical experimentation
- Vietnamization: 1971-1973, as the mission shifted back to training, advising, and supporting South Vietnamese units.
Hanyok divides the history into periods based on enemy action, while Gilbert divides it on American deployments and changes in technology.[14]US SIGINT support during the Vietnam War came principally from service cryptographic units, with some NSA coordination. Units still belonged to their parent service, such as the Army Security Agency and Naval Security Group. Some SIGINT personnel were assigned to covert special operations and intelligence units.Although SIGINT personnel were present in 1960, Gilbert breaks the ASA involvement in Vietnam into four chronological phases,[13] which do not match the more recent NSA history by Hanyok, which is less focused on events with the US military. [15]
- The Early Years: 1961-1964, characterized by direction-finding and COMSEC, ending with the Gulf of Tonkin Incident. This partially overlaps the period of "SIGINT and the Attempted Coups against Diem, 1960-1962"[15]
- The Buildup: 1965-1967, with cooperation at the Corps/Field Force level, and the integration of South Vietnamese linguists. Major ASA units at this time were the 509th Radio Research Group and 403d RR (Radio Research) SOS (Special Operations Detachment)[13]
- Electronic Warfare: 1968-1970, with substantial technical experimentation
- Vietnamization: 1971-1973, as the mission shifted back to training, advising, and supporting South Vietnamese units.[13]
The NSA History redacted most information, not already public, from 1954 to 1960, but gaps can be filled from other sources A section is titled "Diem's War against Internal Dissent". It opens with an observation that most opposition to President Diem was inflamed by "his program of wholesale political suppression, not just of the Viet Minh cadre that had stayed in the south after Geneva, but against all opposition, whether it was communist or not." By mid-1955, according to Diem, approximately 100,000 Communists were alleged to have surrendered, or rallied to Diem, although the NSA author suggests this did not correspond to political reality, since there were only an estimated 10,000 "stay-behinds". It was clear, however, that the number of communists at large dropped dramatically.
The history mentions that Diem's security organs were given a free hand by Ordnance Number 6 of January 1956, putting anyone deemed a threat to the defense of the state and public safety," at least in house arrest. A quote from Life magazine, generally considered friendly to Diem, suggested that a substantial number of non-communists had been arrested. This is followed by a brief note, "Yet in that same process of neutralizing opposition, Diem set the seeds for his own downfall." This followed by long redactions. Both Diem and the US Military Assistance Advisory Group (MAAG), according to the NSA history, felt the communists were going into "last gasps" in late 1959.[15]
For the period before large-scale U.S. involvement, see National Security Agency and Southeast Asia, 1954-1961.
NSA and Western Counterespionage
For several years, "the fact of" the existence of NSA was not acknowledged, and for many years thereafter, one of the Washington area sayings was that the initials stood for "Never Say Anything", and the physical security of the campus was far greater than that at CIA. In spite of that attitude, however, there were several severe security breaches by staff working as Soviet defectors in place, or people who defected with maximum publicity.
NSA also engaged in questionably legal surveillance of civilian international traffic either originating or terminating in the United States.
Weisband
ASA in the post-World War II period had broken messages used by the Soviet armed forces, police and industry, and was building a remarkably complete picture of the Soviet national security posture. It was a situation that compared favorably to the successes of World War II. Then, during 1948, in rapid succession, every one of these cipher systems went dark, as a result of espionage by a Soviet agent, William Weisband. NSA suggests this may have been the most significant loss in US intelligence history. [9]
Martin and Mitchell
William Martin and Bernon Mitchell were NSA mathematicians, regarded highly for their scientific insight, but generally have been accepted to have odd socialization. [16] In 1960, they left on vacation, and eventually showed up in a Soviet press conference, speaking of the evils of the NSA. At the time, it was widely rumored that they were homosexual, but new evidence suggests while they may have been social misfits, there is little evidence they were gay. The Seattle Times' obtained files that said
"Beyond any doubt," the unnamed author of a then-secret NSA study on the damage done by the defection wrote in 1963, according to the recently released documents, "no other event has had, or is likely to have in the future, a greater impact on the Agency's security program."
Dunlop
Jack Dunlop was, as a member of the military, a courier and driver for the National Security Agency. After retirement, he applied for a civilian job at NSA, but the more intensive security clearance process soon revealed unexplained large income.
He committed suicide before it was fully determined that he was selling documents to the Soviet Union.
Walker Ring
Communications security personnel for the Navy (and Central Security Service), John Walker and a number of family members and friends sold immense amounts of communications security information to the Soviets. The material revealed has often been called the greatest compromise in the history of the United States. He plea-bargained a reduced sentence for his son, but the rest of the ring are lifetime guests of the U.S. Bureau of Prisons.
US domestic surveillance
During this period, several programs, potentially in violation of its foreign intelligence charter, the NSA (and its AFSA predecessor) monitored international telegram and selected voice communications of American citizens[2].Project SHAMROCK, started during the fifties under AFSA, the predecessor of NSA, and terminated in 1975, was a program in which NSA obtained copies, without a warrant, of telegrams sent by international record carriers. The related Project MINARET intercepted voice communications of persons of interest to US security organizations of the time, including Malcolm X, Jane Fonda, Joan Baez, and Martin Luther King.
Western counterespionage
From 1943 to 1980, the VENONA project, principally a US activity with support from Australia and the UK, recovered information, some tantalizingly only in part, from Soviet espionage traffic. See article on VENONA. VENONA gave substantial information on the scope of Soviet espionage against the West, but critics claim some messages have been interpreted incorrectly, or are even false. Part of the problem is that certain persons, even in the encrypted traffic, were identified only by code names such as "Quantum". Quantum was a source on US nuclear weapons, and is often considered to be Julius Rosenberg. The name, however, could refer to any of a number of spies.
Collection methods advance
Before satellite SIGINT was practical, US information about Soviet radar stopped about 200 miles inland from the coastline. After these space systems went into service, effectively all radars on the Soviet landmass became known to NSA. They informed the Strategic Air Command with the technical details and locations of air defense radars, which went into planning attack routes of the Single Integrated Operational Plan (SIOP), the master set of plans for nuclear warfare. They provided operational information to Navy commanders. Coupled with IMINT from CORONA, they helped CIA, DIA and other elements of the intelligence community understand the overall Soviet threat.
There were still specific cases where aircraft were needed -- and where crews died. UAVs became increasingly more attractive for such high-risk missions.
Space systems begin
The first successful SIGINT satellites, known informally as "Ferrets", were classified payloads aboard the Galactic Radiation and Background (GRAB), designed by the U.S. Naval Research Laboratory. GRAB had an unclassified experiment called Solrad, and an ELINT package called TATTLETALE. See National Reconnaissance Office (NRO), an agency even more secretive than NSA for more detail on GRAB/TATTLETALE. As the military cryptologic agencies, using ground, sea, and aircraft platforms, actually intercepted and processing raw SIGINT material to be forwarded to Fort Meade, the NRO was responsible for similar capture, but from satellites that NRO was responsible for launching and operating.
According to the NRO, the incremental upgrade of GRAB's Tattletale package was POPPY. The second program, Poppy, operated from 1962 to 1977. The "fact of" the Poppy program, along with limited technical information, was declassified in 2004. [17] At least three NRO operators did the preliminary processing of the POPPY data, one measuring the orbital elements of the satellite and the selected polarization, while the second operator identified signals of interest. The third operator did more detailed, non-real-time, analysis of the signal, and transmitted information to NSA.
After these space systems went into service, most radars on the Soviet landmass became known to NSA. NSA, in turn, provided the characteristics of the Soviet air defense network to the Single Integrated Operational Plan (SIOP) staff, and to Navy commanders who would operate in Soviet waters. Coupled with IMINT from CORONA, they helped CIA, DIA and other elements of the intelligence community understand the overall Soviet threat.
The U.S. embarked on a new generation of reconnaissance satellites, Air Force Project WS-117L, approved by President Dwight D. Eisenhower in 1954. This program was focused on IMINT and MASINT, but some satellites would also carry signal intercept subsystem under Project PIONEER FERRET. [18] By 1959, WS-117L had split into three programs: [19] The major programs were:
- Discoverer, the unclassified name for the CORONA IMINT satellite
- Satellite and Missile Observation System (SAMOS)(IMINT)
- Missile Defense Alarm System (MIDAS), a nonimaging staring infrared MASINT system
The first experimental ELINT package would fly aboard a photoreconnaissance satellite, Discoverer-13, in August 1960. Translated from the Russian, it was equipped with "Scotop equipment was intended to record the signals of Soviet radars which were tracking the flight of American space objects." [18]
Soviet sources state the first specialized ELINT satellites, which received the designation of "Ferret," was begun in the USA in 1962.[18] In actuality, the first successful SIGINT satellite was the U.S. Navy's Galactic Radiation and Background (GRAB), designed by the U.S. Naval Research Laboratory. GRAB had an unclassified experiment called Solrad, and an ELINT package called Tattletale. Tattletale was also called Canes; CANES was also the National Reconnaissance Office (NRO) sensitive compartmented information (SCI) codeword for the control system overall program. GRAB intercepted radar pulses as they came over the horizon, translated the frequency, and retransmitted each pulse, with no further processing, to ground receiving sites.[17] GRAB operated from 1960 to 1962.[20] Again examining space-based SIGINT through Soviet eyes, "The tasks of space-based SIGINT were subdivided into two groups: ELINT against antiaircraft and ABM radars (discovery of their location, operating modes and signal characteristics) and SIGINT against C3 systems. In order to carry out these tasks the US developed ... satellites of two types:
- small ELINT satellites which were launched together with photoreconnaissance satellites into initially low orbits and then raised into a polar working orbit at an altitude of 300 to 800 km using on-board engines
- heavy (1 to 2 tonne mass) "SIGINT" (possibly the translator's version of COMINT?) satellites, which were put into orbit at an altitude of around 500 km using a Thor-Agena booster. The Soviet source described the satellites of the late sixties as "Spook Bird" or CANYON [18], which was the predecessor to the production Rhyolite platforms. This was not completely correct if the Soviets thought these were heavy ELINT satellites; CANYON was the first COMINT satellite series, which operated from 1968 to 1977.
According to the NRO, the incremental upgrade of GRAB's Tattletale package was POPPY. The second program, Poppy, operated from 1962 to 1977. The "fact of" the Poppy program, along with limited technical information, was declassified in 2004. [17] At least three NRO operators did the preliminary processing of the POPPY data, one measuring the orbital elements of the satellite and the selected polarization, while the second operator identified signals of interest. The third operator did more detailed, non-real-time, analysis of the signal, and transmitted information to NSA.
In the EC-121 shootdown incident of 15 April 1969, an EC-121M of the U.S. Navy's Fleet Airborne Reconnaissance Squadron One (VQ-1) Vietnam, took off on a routine SIGINT patrol under the BEGGAR SHADOW program. North Korean air search radar was monitored by the USAF 6918th Security Squadron in Japan, and Detachment 1 6922nd Security Wing at Osan Air Base in Korea, and the Naval Security Group at Kamiseya, Japan. The EC-121M was not escorted. When US radar detected the takeoff of North Korean interceptors, and the ASA unit lost touch, ASA called for fighters, but the EC-121M never again appeared on radar. 31 crewmen were lost.
In response to this threat on what had been considered a low-risk mission, Ryan was tasked to develop the AQM-34Q as the SIGINT version of the AQM-34P, with antennas along the fuselage. Underwing fuel tanks were added to this model, and the AQM-34R updated the electronics and had standard underwing tanks.[21] Still, some missions still need to be flown by manned aircraft.
CIA provides additional collection approaches
While the Service Cryptologic Elements (SCE) provided intercepts from ground, air and sea platforms were U.S. overt forces could go, and NRO provided satellite basis, cooperation between NSA and CIA's clandestine operations personnel found ways to emplace, secretly, SIGINT sensors behind the Iron Curtain.
Also in 1962, the Central Intelligence Agency, Deputy Directorate for Research, formally took on ELINT and COMINT responsibilities[22]. "The consolidation of the ELINT program was one of the major goals of the reorganization....it is responsible for:
- Research, development, testing, and production of ELINT and COMINT collection equipment for all Agency operations.
- Technical operation and maintenance of CIA deployed non-agent ELINT systems.
- Training and maintenance of agent ELINT equipments
- Technical support to the Third Party Agreements.
- Data reduction of Agency-collected ELINT signals.
- ELINT support peculiar to the penetration problems associated with the Agent's reconnaissance program under NRO.
- Maintain a quick reaction capability for ELINT and COMINT equipment."
"CIA's Office of Research and Development was formed to stimulate research and innovation testing leading to the exploitation of non-agent intelligence collection methods....All non-agent technical collection systems will be considered by this office and those appropriate for field deployment will be so deployed. The Agency's missile detection system, Project [deleted] based on backscatter radar is an example. This office will also provide integrated systems analysis of all possible collection methods against the Soviet antiballistic missile program is an example." [22]. It is not clear where ELINT would end and MASINT would begin for some of these projects, but the role of both is potentially present. MASINT, in any event, was not formalized as a US-defined intelligence discipline until 1986.
US Submarine SIGINT begins
Under the code names HOLYSTONE, PINNACLE, BOLLARD, and BARNACLE, began in 1959, US submarines infiltrated Soviet harbors to tap communications cables and gather SIGINT. They also had a MASINT mission against Soviet submarines and missiles. The program, which went through several generations, ended when compromised, by Ronald Pelton, in 1981.[23]
Early UAV development
Unmanned aerial vehicle (UAV), called "drones" at the time, were introduced quite early and served a number of purposes, although SIGINT was not the first mission. [21] won the US Air Force competition for the Q-2 jet-propelled aerial target. Known as the Q-2A Firebee, the jet-propelled UAV, launched by a rocket and recovered by parachute, was also bought by the Navy and Army.
In 1961, the Air Force requested a reconnaissance version of what was then designated the BQM-34A, which resulted in the Firebee Model 147A, to be designated the AQM-34.[21] This UAV looked like its target version, but carried more fuel and had a new navigation system. These reconnaissance drones were air-launched from a DC-130 modified transport. Like all subsequent versions of this UAV, it was air-launched from underneath the wing of a specially modified Lockheed DC-130 Hercules, rather than ground-launched with rocket assistance. These are thought to have been operationally for IMINT, although SIGINT was considered, as more aerial US reconnaissance platforms do SIGINT than IMINT, and most IMINT platforms, such as the U-2 and SR-71 also have SIGINT capability. Drones of this version were to be used in the Cuban Missile Crisis.[21]
The Cuban Crisis and the hotter part of the Cold War
While the start of the Cuban Missile Crisis came from IMINT showing Soviet missiles under construction, SIGINT had had an earlier role in suggesting that increased surveillance of Cuba might be appropriate. NSA had intercepted suspiciously blank shipping manifests to Cuba, and, through 1961, there was an increasing amount of radio chatter suggestive of Cuba receiving both Soviet weapons and personnel. The weapons could be used offensively as well as defensively[24].
In September and October 1962, SIGINT pointed to the completion of a current Soviet air defense network in Cuba, presumably to protect something. The key U-2 flight that spotted the ballistic missiles took place on October 15. While the IMINT organizations were most critical, an anecdote of the time, told by Juanita Moody, the lead SIGINT specialist for Cuba, that the newly appointed Director of NSA, LTG Gordon Blake, came by to see if he could help. "She asked him to try to get additional staff to meet a sudden need for more personnel. Shortly she heard him on the telephone talking to off-duty employees: "This is Gordon Blake calling for Mrs. Moody. Could you come in to work now?"
Two RB-47H aircraft, of the 55th Reconnaissance Wing, during the Cuban Missile Crisis were modified to work with Ryan AQM-34 SIGINT UAVs,[21] still launched from DC-130s. The UAVs carried deceptive signal generators that made them appear to be the size of a U-2, and also carried receivers and relays for the Soviet SA-2 surface-to-air missiles on Cuba. In real time, the UAVs relayed the information to the RB-47, which was itself using ELINT sensors against the radar and SA-2 command frequencies. Essentially, the UAV was carrying out a "ferret" probe intended to provoke defensive response, but not jeopardizing the lives of pilots. This full capability was only ready in 1963, and the original scenario no longer held.
During the Crisis, after a U-2 was shot down, RB-47H's of the 55th wing began flying COMMON CAUSE missions, with other US aircraft, to identify any Cuban site that fired on a US plane. The Cubans, however, believed the US threat that such a site would immediately be attacked, and withheld their fire. Crews began calling the mission, as a result, "Lost Cause".[25]
Tactical Naval SIGINT monitored stopped Soviet transports, when it was unknown if they would challenge the naval quarantine. Direction finding confirmed they had turned around. [24]
While certain drone functions failed in the Cuban crisis, they were soon ready for service. DC-130 launchers and controllers were deployed to Kadena in Okinawa, and the Bien Hoa in Vietnam. The real-time telemetry, hoped for during the Cuban crisis, was now a reality, and RB-47H ELINT aircraft were dedicated to Southeast Asian operations.
RC-135Ms were flying at the same time, but primarily against China and Russia. Eventually, their missions focused on Southeast Asia.[25]
US-RVN doctrine, 1961
In January 1961, while the Vietnam embassy and military group prepared a counterinsurgency plan, the SIGINT community did its own planning. The first review of the situation assumed limited support to the ARVN COMINT teams. Essentially, the policy was that the South Vietnamese would be trained in basic direction finding using "known or derived" technical information, but, for security reasons, COMINT that involved more sophisticated analysis would not be shared. It was also felt that for at least the near term, ARVN COMINT could not provide meaningful support, and the question was presented, to the State Department, if it was politically feasible to have US direction-finding teams operate inside South Vietnam. The March 1961 plan included both tactical support and a strategic COMINT mission collection NVA data for NSA.
Eventually, the idea was that the South Vietnamese could intercept, but send the raw material to the US units for analysis. Two plans were created, WHITEBIRCH to increase US capability throughout the region but emphasizing South Vietnam, and SABERTOOTH to train ARVN personnel in basic COMINT. Concerns over ARVN security limited the information given them to non-codeword SECRET information. The first step in WHITEBIRCH was the 400th ASA Special Operations Unit (Provisional), operating under the cover name of the 3rd Radio Research Unit (RRU).[14]
The 3rd RRU soon had its first casualty, SP4 James T. Davis, killed in an ambush.[13] Soon, it was realized that thick jungle made tactical ground collection exceptionally dangerous, and direction-finding moved principally to aircraft platforms[26].
Drones evolve(1967-1971)
A major advance for high-risk IMINT and SIGINT missions was the high-altitude AQM-34N[21] COMPASS DAWN, which flew as high as 70000 ft and had a range over 2,400 miles. AQM-34N's flew 138 missions between March 1967 and July 1971, and 67% were parachute-recovered with the new Mid-Air Retrieval System, which used a helicopter to grab the parachute cable in mid-air. While this had an IMINT mission, the potential of high altitude for SIGINT over a wide area was obvious.
In the EC-121 shootdown incident of 15 April 1969 , an EC-121M of the U.S. Navy's Fleet Airborne Reconnaissance Squadron One (VQ-1) Vietnam, took off on a routine SIGINT patrol under the BEGGAR SHADOW program. North Korean air search radar was monitored by the USAF 6918th Security Squadron in Japan, and Detachment 1 6922nd Security Wing at Osan Air Base in Korea, and the Naval Security Group at Kamiseya, Japan. The EC-121M was not escorted. When US radar detected the takeoff of North Korean interceptors, and the ASA unit lost touch, ASA called for fighters, but the EC-121M never again appeared on radar. 31 crewmen were lost.
In response to this threat on what had been considered a low-risk mission, Ryan was tasked to develop the AQM-34Q was the SIGINT version of the AQM-34P, with antennas along the fuselage. Underwing fuel tanks were added to this model, and the AQM-34R updated the electronics and had standard underwing tanks.[21]
1980s
Strategic SIGINT satellites for NSA
From 1972 to 1989, low earth orbit SIGINT satellites were launched only as secondary payloads with KH-9 and KH-11 IMINT satellites. They were code-named after female sex symbols, such as RAQUEL, FARRAH, BRIDGET and MARILYN.[23]
Four geosynchronous RHYOLITE satellites were launched in the seventies, with COMINT and TELINT missions.[27] These were reported to be directed against line-of-sight microwave, telemetry, or both. Their signals downlinked to Pine Gap station in Alice Springs, Australia. According to Encyclopedia Astronautica, the downlink was in a remote location, to prevent Soviet or Chinese SIGINT personnel from intercepting the downlink, and, in turn, discovering the targeting of the satellites. Downlinked data was then encrypted and retransmitted to NSA at Fort Meade, MD.
The project became unusually public as it was the key element in the espionage trial of the 'Falcon and the Snowman', Boyce and Lee. Rhyolite was also known as Program 720, Program 472, and Aquacade. After having the name compromised when Christopher Boyce sold information to the Soviets, the code name was changed to AQUACADE. In the late seventies, another class of geosynchronous SIGINT satellites, first called CHALET and renamed VORTEX after the code name was compromised. After the loss of Iranian monitoring stations, these satellites were also given an TELINT capability.[23]
JUMPSEAT ELINT satellites, using a Moliyna orbit, started launching in 1975.[23] Their launch parameters were very similar to the SDS communications satellites used for connectivity in high latitudes, and individual launches could easily have been either JUMPSEAT or SDS.[28] While the primary mission of JUMPSEAT constellations appeared to be microwave COMINT, they may also have had ELINT capabilities.
1980s
This was a decade of world change, with changes in Cold War emphasis and alliances, the first submarine attack since World War II in the context of a regional war involving extensive power projection, low- and medium-intensity operations, and continuing national policy development.
1980s Cold War SIGINT
Roughly from the late 1980s on, there was cooperation between the US and the PRC in collecting SIGINT of mutual interest, principally against Russia [29]. It is believed that the Qitai and Korla sites, in Xinjiang (Sinkiang) are operated jointly by the Chinese and the US CIA Office of SIGINT Operations against Soviet missile tests and space launches, but their current status is uncertain. It is also unclear if the Office of SIGINT Operations is still part of CIA, or if NSA may operate these sites.
Spruance-class destroyers sailed on collection missions in the Black Sea, Baltic Sea, and off the coast of Libya, a Soviet client.[23]
1980s Falklands War SIGINT
Under the UKUSA Agreement, Great Britain called upon NSA SIGINT satellite resources to collect relevant information. Tension existed because the controversial British investigative journalist, Duncan Campbell, had published information considered sensitive. According to one former British SIGINT officer, "We can ask the Americans to do things, but we cannot compel them. There may be targets they don't want to cover. The Falklands was a factor here. It brought going it alone back into fashion."[30]
1980s strategic SIGINT policy
In 1980, U.S. intercepts of Soviet communications generated a fear that the Soviets were about to invade Iran. In 1983 intercepts allowed the United States to piece together the details concerning the sinking of a Soviet submarine in the North Pacific.
In 1983 it began an all-source program targeting Soviet prison camp system, with the specific intent of issuing a study that would embarrass the Soviets[23].
MAGNUM geosynchronous SIGINT satellites were first launched from the Space Shuttle in 1985. These were believed to be more sensitive and perhaps stealthier than RHYOLITE/AQUACADE.
After the Liberty and Pueblo incidents, only combatant ships, destroyers and frigates, were used for collection missions. In addition to SIGINT intercept against the Soviets, combatant ships operated off Nicaragua, El Salvador, and Honduras. One purpose-built SIGINT auxiliary, the ARL-24 Sphinx, generally stayed off the Nicaraguan coast.
1990s
Terrorism from foreign groups became an increasingly major concern, as with the 1992 al-Qaeda attack in Yemen, the 1993 truck bombing of the World Trade Center, 1995 (Saudi communications center) and 1996 (Khobar Towers) in Saudi Arabia, and the 1998 bombings of the US embassies in Dar es Salaam, Tanzania and Nairobi, Kenya. Third world and non-national groups, with modern communications technology, in many ways are a harder SIGINT target than a nation, such as Russia or China, that sends out large amounts of traffic. According to the retired Commandant of the US Marines, Alfred M. Gray, Jr., some of the significant concerns of these targets are:
- Inherently low probability of intercept/detection (LPI/LPD) because off-the-shelf radios can be frequency agile, spread spectrum, and transmit in bursts.
- Additional frequencies, not normally monitored, can be used. These include citizens band, marine (MF, HF, VHF) bands, and higher frequencies for short-range communications
- Extensive use of telephones, almost always digital. Cellular and satellite telephones, while wireless, are challenging to intercept, as is Voice over IP (VoIP)
- Commercial strong encryption for voice and data
- "Extremely wide variety and complexity of potential targets, creating a "needle in the haystack" problem" [31]
2000s
As evidenced by the Hainan Island incident, even while China and the US may cooperate on matters of mutual concern towards Russia, the Cold War has not completely disappeared.
There was more regional cooperation, often driven by concerns about transnational terrorism. European countries also are finding that by sharing the cost, they can acquire SIGINT, IMINT, and MASINT capabilities independent of the US.
In the US, both communications security and COMINT policies have been evolving, some with challenges. The adoption of a Belgian-developed encryption algorithm, approved in a public process, and accepted both for sensitive but unclassified traffic, as well as for classified information sent with NSA-generated and maintained keys, redraws the cryptologic environment as no longer NSA or not-NSA. Controversy continues on various types of COMINT justified as not requiring warrants, under the wartime authority of the President of the United States.
Technologically, there was much greater use of UAVs as SIGINT collection platforms.
Hainan Island incident
In 2001, a US EP-3 SIGINT aircraft had a midair collision with a shadowing Chinese fighter, in what has become known as the Hainan Island incident. Both sides blamed the other, although the US claimed the aircraft was in international airspace, a reasonable assumption given the amount of navigational instrumentation it carries. The fighter pilot died, and the EP-3 made an emergency landing in China, erasing as much sensitive information as possible. While the Chinese did not release the aircraft for several months, the crew having been released earlier, the most sensitive information was not so much the aircraft's instrumentation, but the signals it was targeting and the reference material about the Chinese "electronic order of battle".
Cryptologic expertise outside NSA
The US government withdrew the last approvals for the Data Encryption Standard, approved for unclassified use in 1976 but now considered quite vulnerable. Its replacement, the Advanced Encryption Standard (AES) was approved in 2002. AES, when used with NSA-supplied keys, is approved for TOP SECRET traffic as well as unclassified, and may be considered a reference point for strong commercial encryption. AES appears, at the present time, to be secure when used properly, which represents a major change in US policy about the availability of strong communications security. Not all governments will allow the use of such strong ciphers.
That the algorithm chosen came from Europe points to a more multilateral world with respect to communications security. AES was developed by two Belgian cryptographers, Joan Daemen and Vincent Rijmen, and submitted to the AES selection process under the name "Rijndael", a portmanteau of the names of the inventors.
Terrorism and response in the US
As a result of the 9/11 attacks, intensification of US intelligence efforts, domestic and foreign, were to be expected. A key question, of course, was whether US intelligence could have prevented or mitigated the attacks, and how it might prevent future attacks. It should be noncontroversial that there will be a delicate balance of intelligence and civil liberties issues.
SIGINT and the 9/11 attacks
In a statement to a joint meeting of the House and Senate Intelligence Committees, NSA Director LTG Michael Hayden said "NSA had no SIGINT suggesting that al-Qa'ida was specifically targeting New York and Washington, D.C., or even that it was planning an attack on U.S. soil. Indeed, NSA had no knowledge before 9/11 that any of the attackers were in the United States....
"We are digging out of a deep hole. NSA downsized about one-third of its manpower and about the same proportion of its budget in the decade of the 1990s. That is the same decade when packetized communications (the e-communications we have all become familiar with) surpassed traditional communications. That is the same decade when mobile cell phones increased from 16 million to 741 million an increase of nearly 50 times. That is the same decade when Internet users went from about 4 million to 361 million an increase of over 90 times. Half as many landlines were laid in the last six years of the 1990s as in the whole previous history of the world. In that same decade of the 1990s, international telephone traffic went from 38 billion minutes to over 100 billion. This year, the world's population will spend over 180 billion minutes on the phone in international calls alone.
"throughout the summer of 2001 we had more than 30 warnings that something was imminent. We dutifully reported these, yet none of these subsequently correlated with terrorist attacks. The concept of "imminent" to our adversaries is relative; it can mean soon or imply sometime in the future"[32]
References
- ↑ National Security Agency, Mission Statement
- ↑ 2.0 2.1 2.2 Senate Select Committee to Study Government Operations with Respect to Intelligence Activities (OCTOBER 29 AND NOVEMBER 6, 1975), The National Security Agency and Fourth Amendment Rights. Retrieved on 2007-12-07
- ↑ National Security Agency/Central Security Service (27 July 1993), United States Signals Intelligence Directive (USSID) 18
- ↑ Under Secretary of Defense for Policy (December 1982), Department of Defense Regulation 4240.1-R: Procedures governing the activities of DOD intelligence components that affect United States persons
- ↑ United States Attorney General (18 April 1983), Attorney General Guidelines for FBI Foreign Intelligence Collection and Foreign Counterintelligence Investigations
- ↑ 6.0 6.1 Singel, Ryan (04.07.06), "Whistle-Blower Outs NSA Spy Room", Wired, ATTWired
- ↑ 7.0 7.1 Hanyok, Robert J. (2002), Chapter 1 - Le Grand Nombre Des Rues Sans Joie: [Deleted and the Franco-Vietnamese War, 1950-1954], Spartans in Darkness: American SIGINT and the Indochina War, 1945-1975, Center for Cryptologic History, National Security Agency
- ↑ 8.0 8.1 Thomas L. Burns (1990), The Origins of the National Security Agency, 1940-1952, National Security Agency
- ↑ 9.0 9.1 9.2 Hatch, David A.; Robert Louis Benson. The Korean War: The SIGINT Background. National Security Agency.
- ↑ Bamford, James (2001). Body of Secrets: Anatomy of the Ultra-Secret National Security Agency. Doubleday.
- ↑ Clive, Keith P. (2002), NSA’s Central Security Service
- ↑ John, Pike, DGSE - General Directorate for External Security (Direction Generale de la Securite Exterieure)
- ↑ 13.0 13.1 13.2 13.3 13.4 13.5 13.6 13.7 Gilbert, James L. (2003). (Review of) The Most secret War: Army Signals Intelligence in Vietnam.. Pittsburgh, PA: Military History Office, US Army Intelligence and security Command..
- ↑ 14.0 14.1 14.2 Hanyok, Robert J. (2002), Chapter 3 - "To Die in the South": SIGINT, the Ho Chi Minh Trail, and the Infiltration Problem, [Deleted 1968], Spartans in Darkness: American SIGINT and the Indochina War, 1945-1975, Center for Cryptologic History, National Security Agency
- ↑ 15.0 15.1 15.2 15.3 15.4 15.5 15.6 Hanyok, Robert J. (2002), Chapter 2 - The Struggle for Heaven's Mandate: SIGINT and the Internal Crisis in South Vietnam, [Deleted 1962], Spartans in Darkness: American SIGINT and the Indochina War, 1945-1975, Center for Cryptologic History, National Security Agency
- ↑ Anderson, Rick (July 18, 2007), Seattle Weekly
- ↑ 17.0 17.1 17.2 MacDonald, Sharon K. & Moreno (2005), Raising the Periscope... Grab and Poppy, America's early ELINT Satellites, U.S. National Reconnaissance Office
- ↑ 18.0 18.1 18.2 18.3 Andronov, A. (1993), Thomson, Allen (translator), ed., "American Geosynchronous SIGINT Satellites", Zarubezhnoye voyennoye obozreniye
- ↑ U.S. Air Force, Chapter V, Space Systems
- ↑ Hall, R. Cargill, The NRO at Forty: Ensuring Global Information Supremacy
- ↑ 21.0 21.1 21.2 21.3 21.4 21.5 21.6 RYAN AQM-34G - R.
- ↑ 22.0 22.1 Central Intelligence Agency (May 1998), Deputy Director for Research
- ↑ 23.0 23.1 23.2 23.3 23.4 23.5 Jeffrey Richelson (1989), The US Intelligence Community, 2nd Edition, Chapter 8, Signals Intelligence, Richelson 1989
- ↑ 24.0 24.1 Johnson, Thomas R. & David A. Hatch (May 1998), NSA and the Cuban Missile Crisis
- ↑ 25.0 25.1 Bailey, Bruce M (1995), The RB-47 and RC-135 in Vietnam
- ↑ Knight, Judson, Army Security Agency
- ↑ , Rhyolite, Encyclopedia Astronautica
- ↑ , Jumpseat, Encyclopedia Astronautica
- ↑ Association of Former Intelligence Officers (16 April 2001]]), China SIGINT Capabilities, ChineseSIGINT
- ↑ Mark Urban, UK Eyes Alpha: the Inside Story of British Intelligence. Chapter 5: Zircon, Urban 1996
- ↑ Gray, Alfred M. (Winter 1989- 1990). "Global Intelligence Challenges in the 1990s". American Intelligence Journal: 37-41.
- ↑ Joint Hearings of the US House and Senate Intelligence Committees (17 October 2002), Statement of LTG Michael V. Hayden, Director, National Security Agency